Network Segmentation Without Compromise
Transform network security with identity-based microsegmentation that enables Zero Trust in weeks, not years.
Learn How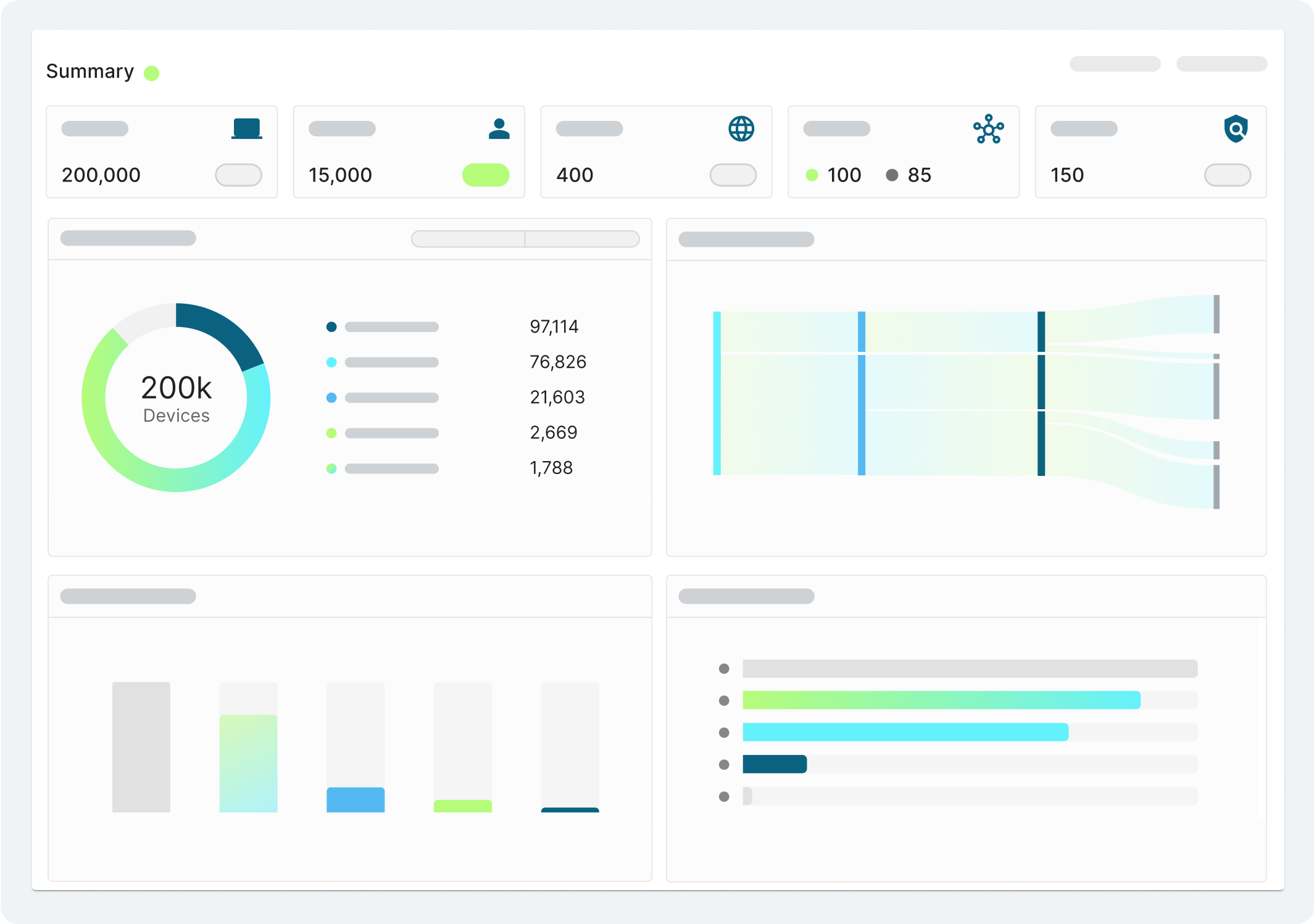
New
Trending
Elisity Named a Cool Vendor in the Gartner® Cool Vendors™ in Cyber-Physical Systems Security 2025
Unlock the InsightsTrusted by Industry Leaders




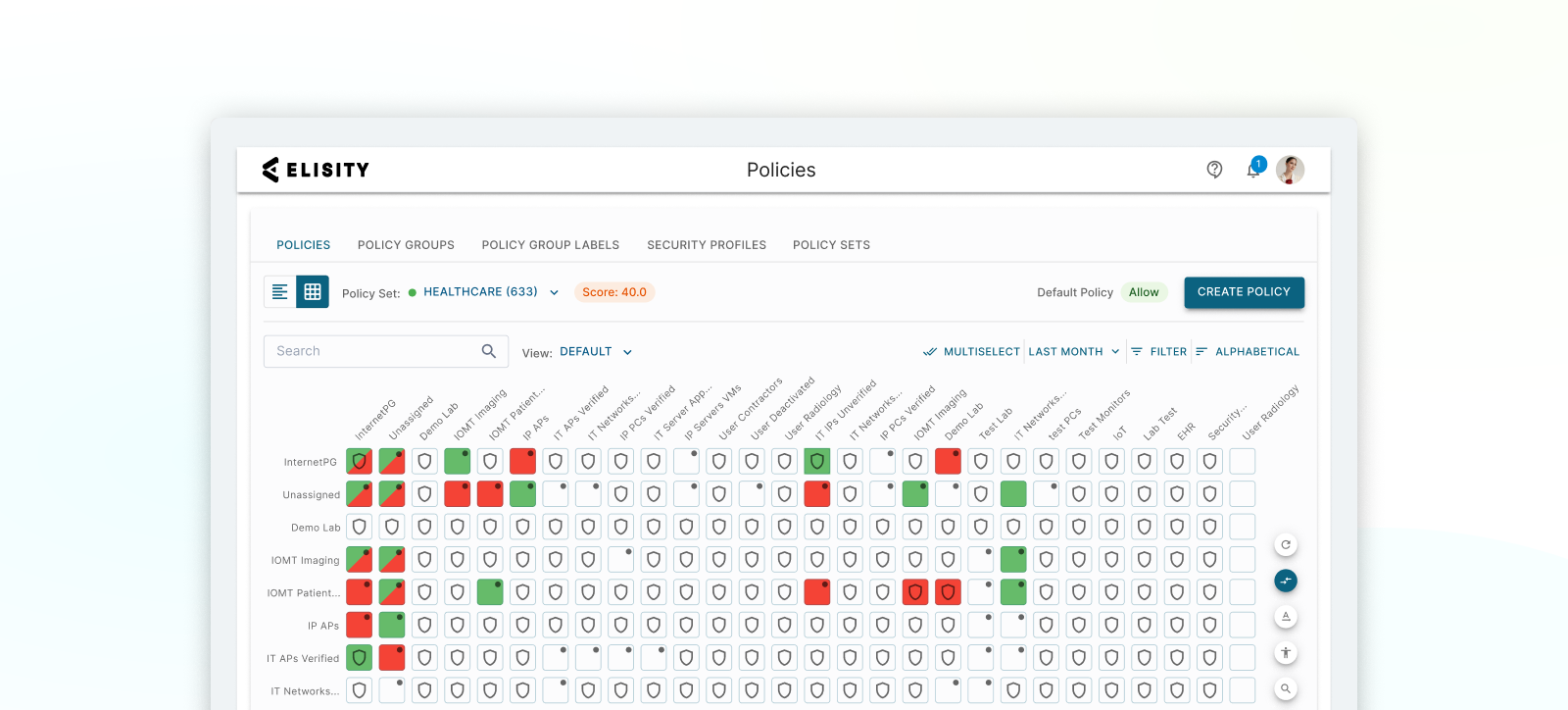
Transform Network Security with Enterprise Scale Microsegmentation
Prevent lateral movement across all users, workloads, and devices without agents, hardware, or network changes.
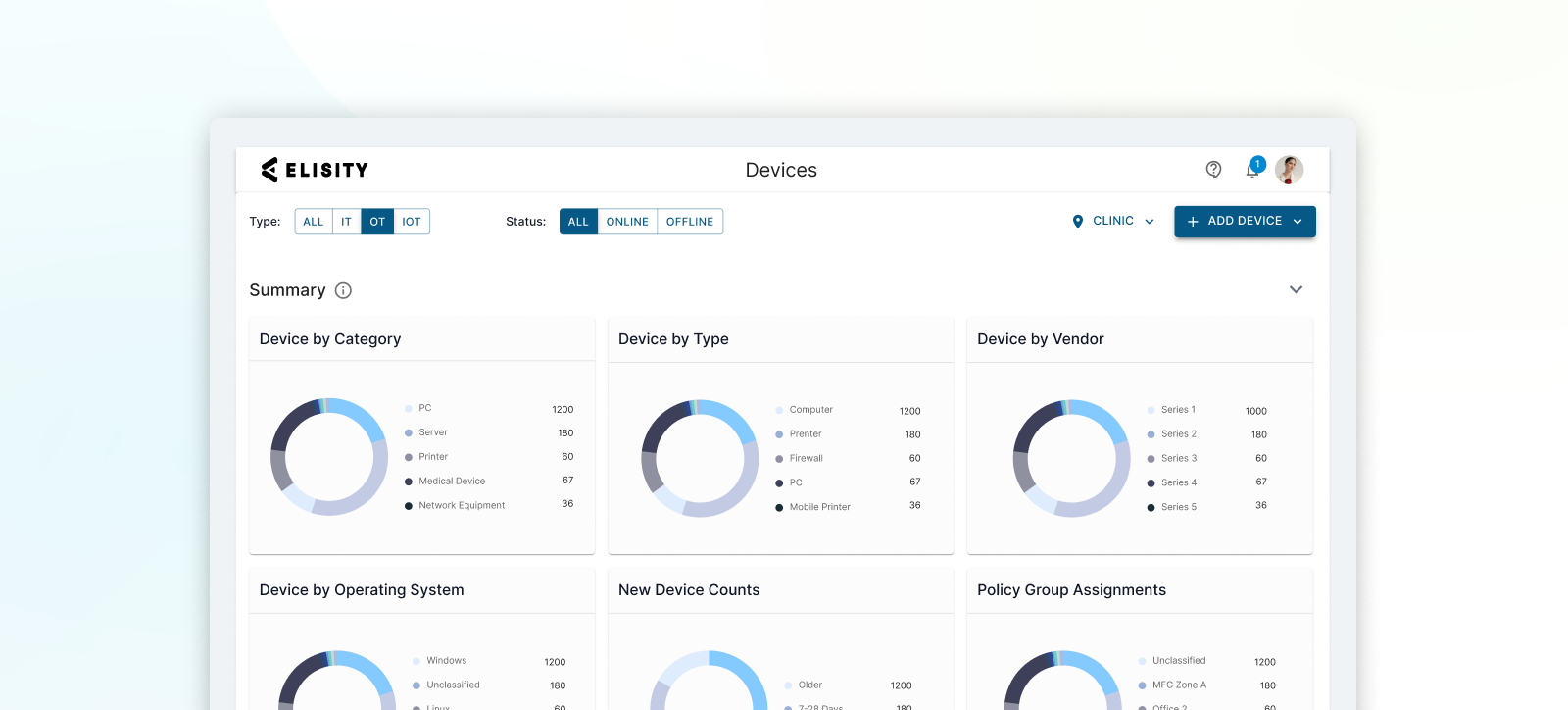
Discover every device, everywhere
Gain full visibility and context of all users, workloads and devices with Elisity IdentityGraph™ intelligence.
.png)
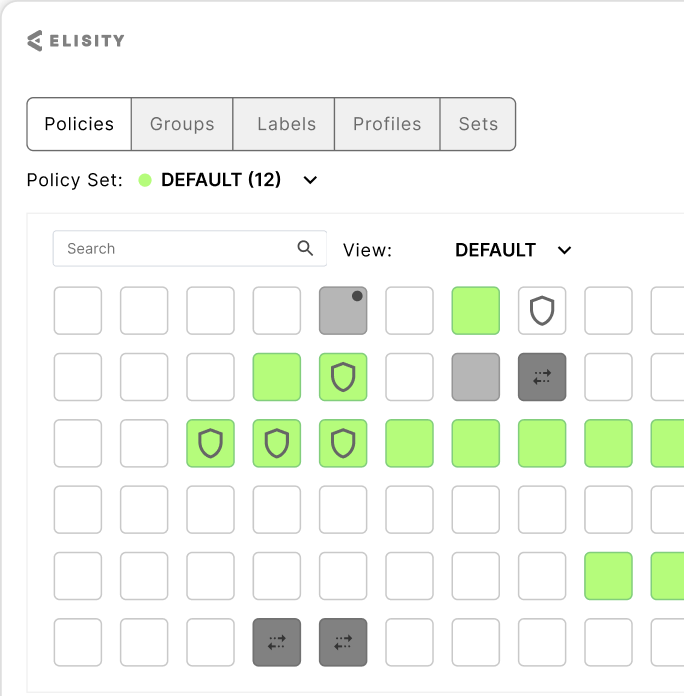
Create and control least privilege access policies
Gain full visibility and context of all users, workloads and devices with Elisity IdentityGraph™ intelligence.
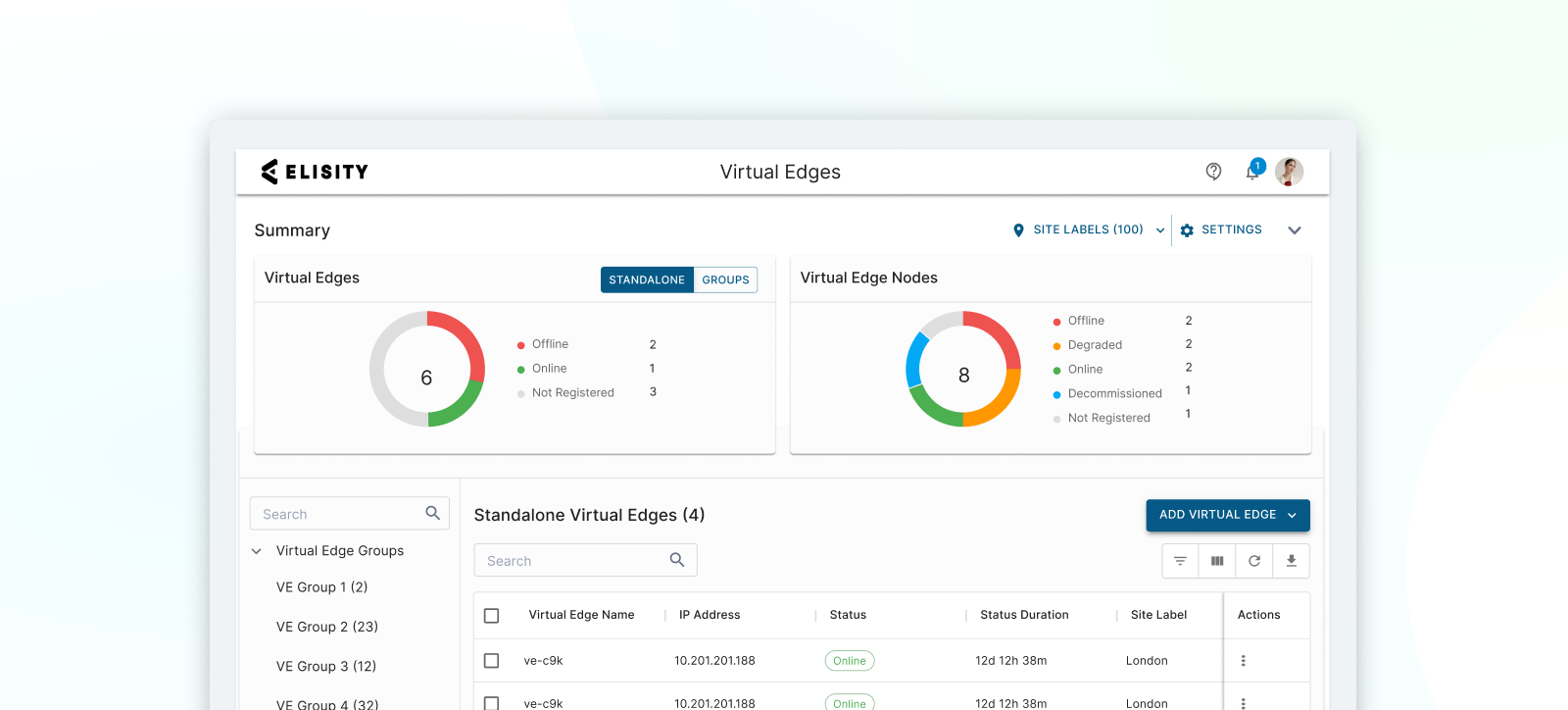
Fast implementation and easy scaling
Streamline operations, align IT, Security and IoT teams. Answer audits quickly.
Case Studies




“With Elisity, we protect our unpatchable medical equipment from ransomware, without disrupting care.”
Jason Elrod, CISO, MultiCare

“Elisity’s deployment at GSK is nothing short of revolutionary, making every other solution pale in comparison.”
Michael Elmore, CISO, GSK

“Elisity has fortified defenses and improved operational efficiency and is a key strategy for accelerating our Zero Trust program.”
Aaron Weismann, CISO, Main Line Health

“In my 30 years of technology & security, I’ve never benefitted so instantly like with Elisity’s tool set.”
Paul Haywood, CISO, Bupa Group

See Elisity’s Deep Domain Expertise Across Industries
Get enterprise-wide protection and simplified management—deployed in weeks using your existing infrastructure. We can help find the right solution for your business, no matter the industry.
-
Healthcare Institutions
-
Manufacturing & Industrial Organizations
-
Commercial Enterprise
-
Healthcare Institutions
Improve Your Hospital and Clinic Network Security with Elisity
From clinical locations to IoMT, protect all users, workloads and devices and patient networks.
-
Manufacturing & Industrial Organizations
Achieve Seamless IT and OT Network Security Policies with Elisity
Strengthen your converged IT and OT environments and meet IEC 62443 requirements.
-
Commercial Enterprise
Finally, Simple Network Segmentation That Works with Elisity
Meet compliance requirements and Zero Trust goals without painful agents and slow rollouts.
-

Healthcare Institutions
Improve Your Hospital and Clinic Network Security with Elisity
From clinical locations to IoMT, protect all users, workloads and devices and patient networks.
-

Manufacturing & Industrial Organizations
Achieve Seamless IT and OT Network Security Policies with Elisity
Strengthen your converged IT and OT environments and meet IEC 62443 requirements.
-

Commercial Enterprise
Finally, Simple Network Segmentation That Works with Elisity
Meet compliance requirements and Zero Trust goals without painful agents and slow rollouts.

Improve Your Hospital and Clinic Network Security with Elisity
From clinical locations to IoMT, protect all users, workloads and devices and patient networks.
Learn More
Achieve Seamless IT and OT Network Security Policies with Elisity
Strengthen your converged IT and OT environments and meet IEC 62443 requirements.
Learn More
Finally, Simple Network Segmentation That Works with Elisity
Meet compliance requirements and Zero Trust goals without painful agents and slow rollouts.
Learn More
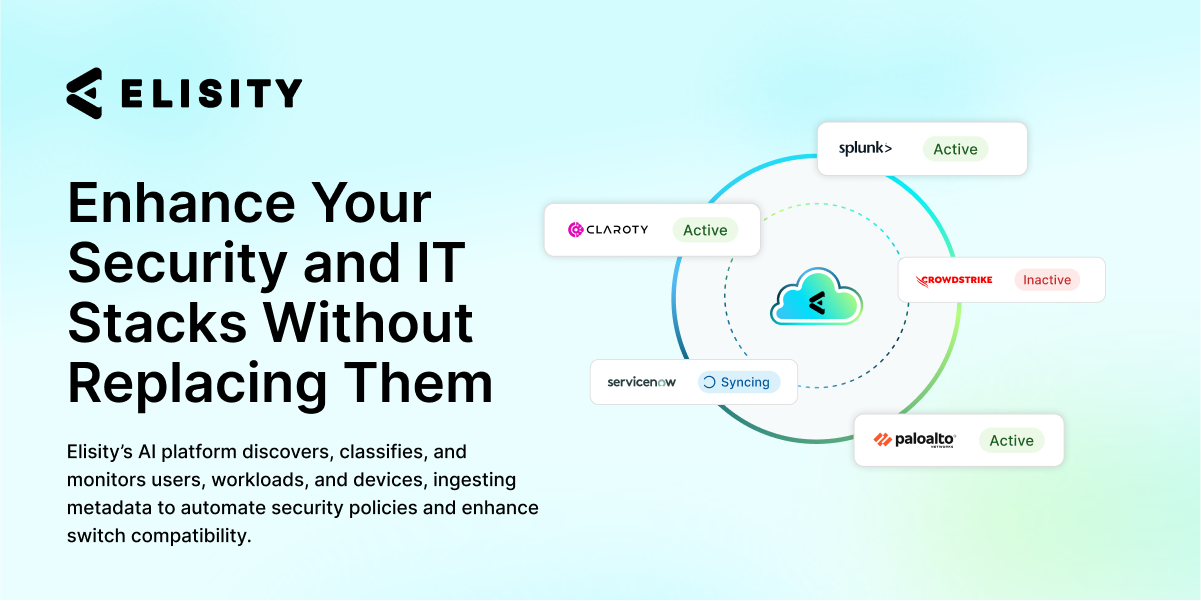
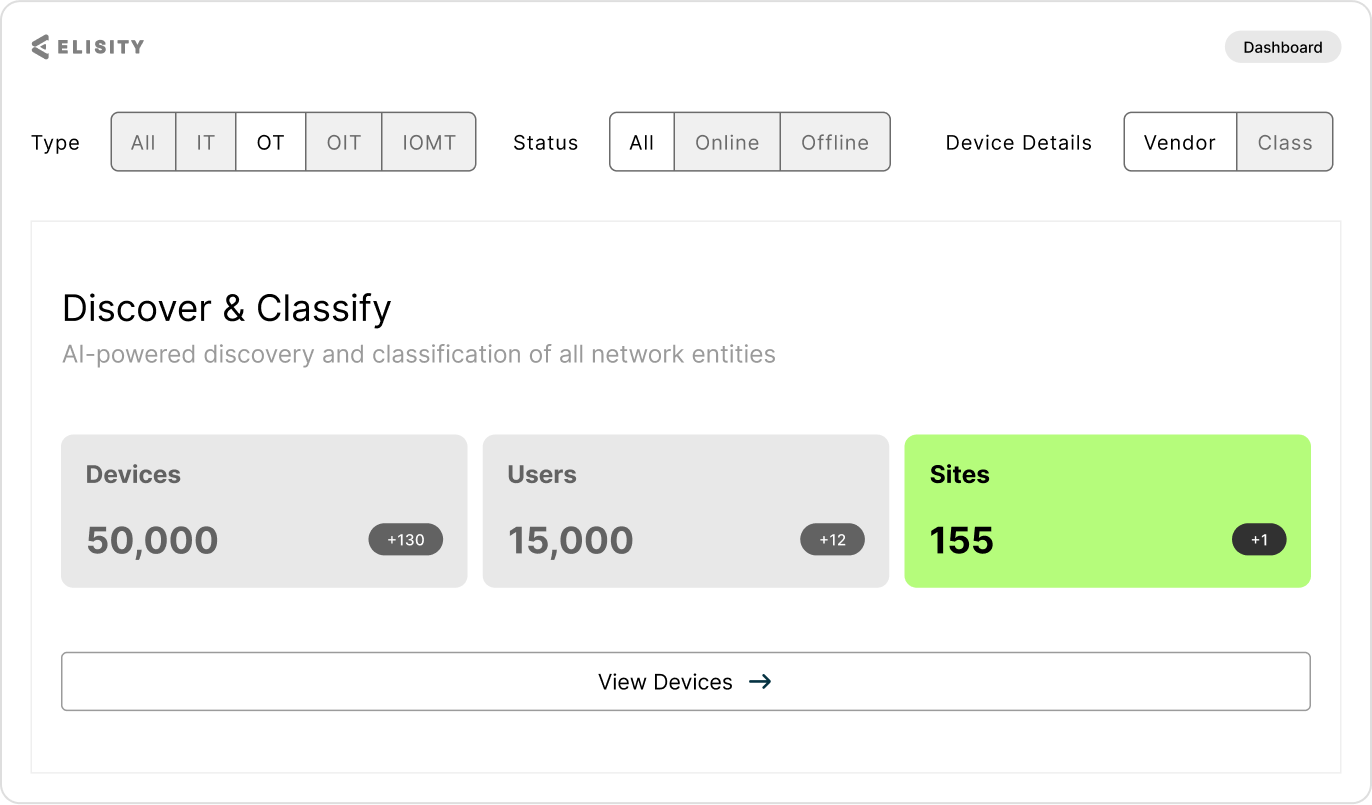
Enhance Your Security and IT Stacks Without Replacing Them
Elisity’s AI platform discovers, classifies, and monitors users, workloads, and devices, ingesting metadata from sources like Active Directory, CrowdStrike, and Armis to automate security policies and enhance switch compatibility.
-
-
-1.png)
-
-1.png)
-
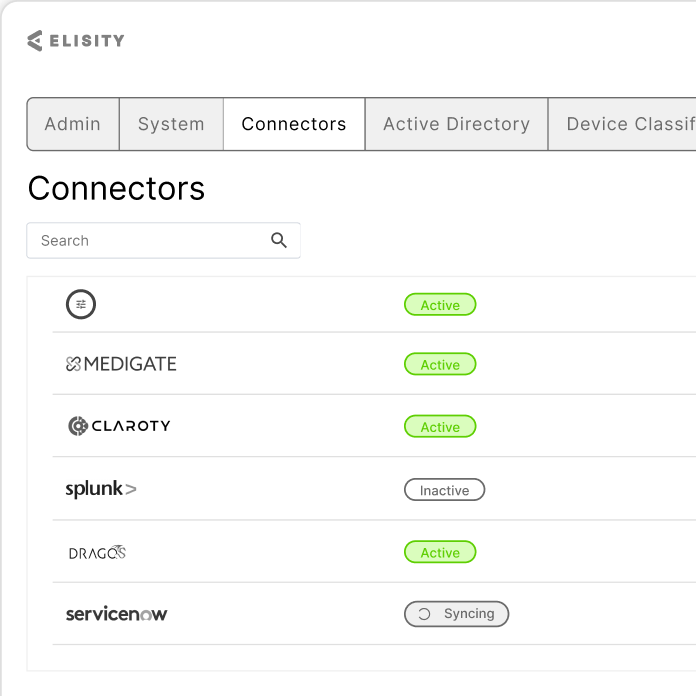
Integrate
Continuously Adapt Policies Using Real-Time Metadata from Your IT and Cybersecurity Stack
Learn More-1.png)
Elisity Platform Capabilities
Elisity Cloud Control Center
An intuitive admin portal for configuring, monitoring, and managing the scale of network security policies. Provides centralized visibility and management of installed Elisity Virtual Edge deployments.
Elisity IdentityGraph™
Creates a real-time, correlated visibility of users, workloads, and devices across your network. Automatically discovers and enriches identity data through multiple sources, enabling confident policy creation and enforcement.
Elisity Dynamic Policy Engine
Creates and enforces granular, context-aware dynamic and static security policies based on identity data and real-time risks. Works seamlessly with IdentityGraph™ to stop lateral movement threats and prevent unauthorized access.
Elisity Intelligence
Analyzes network patterns and metadata to identify vulnerabilities and threats. Provides automated risk scoring, policy recommendations, and continuous monitoring to prevent lateral movement and protect critical assets.
Elisity Virtual Edge
Lightweight container software that runs on existing switches or virtual environments. It synchronizes policies to your existing infrastructure enabling actionable controls and enforcement without requiring additional hardware.
Explore Elisity’s Interactive Demo: See How It Works
Experience how Elisity discovers 99% of all users, workloads, and devices in one day, without agents or network changes. See firsthand how you can create, simulate, and automate least privilege access policies that prevent lateral movement while simplifying audit compliance in just weeks.
Launch Tour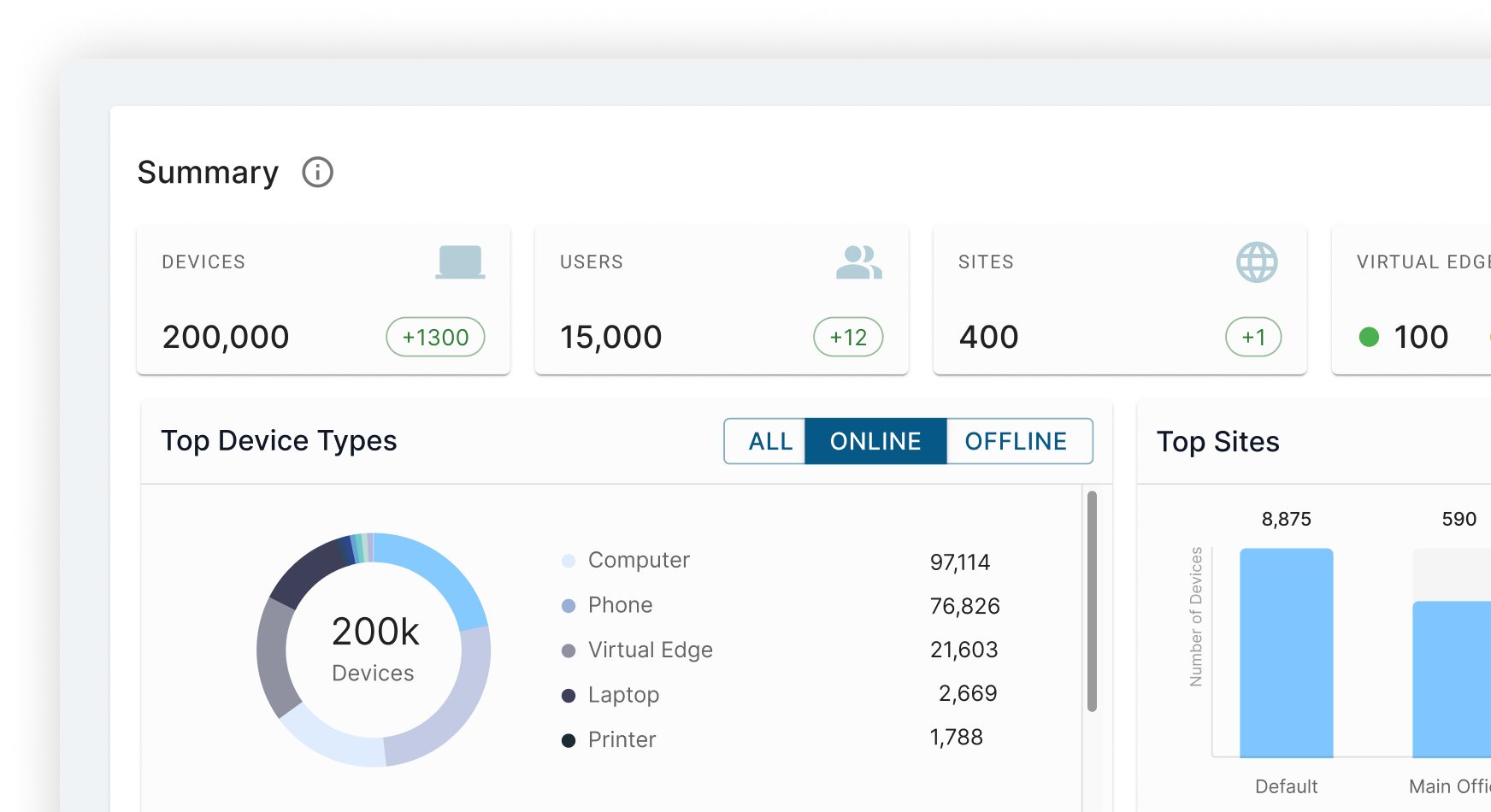
Compliance
Continuous Compliance with Network Segmentation
Meet PCI, HIPAA, IEC 62443, and other regulatory requirements through automated network segmentation that provides detailed audit trails, granular controls, and push-button reporting all while strengthening your security posture.
Explore Compliance Standards



Resources
View All ResourcesReady to Prevent Lateral Movement? Secure Your Network in Weeks, Not Years
Don't wait for attackers to exploit your east-west traffic security policy gaps. Implement Elisity's identity-based microsegmentation without agents, hardware, or network changes. Discover 99% of all users, workloads, and devices in one day, create dynamic least privilege policies, and prevent lateral movement—all while leveraging your existing infrastructure. Schedule your personalized demo today.
Schedule Time With Us