Elisity supports many common compliance frameworks.

NIST Cybersecurity Framework (CSF) 2.0
Coming Soon.

NIST Zero Trust Architecture 800-207
Coming Soon.
Elisity and PCI DSS 4.0
Elisity’s microsegmentation technology is meticulously engineered to align with Payment Card Industry Data Security Standard (PCI DSS) 4.0’s stringent standards, ensuring the highest level of security for cardholder data. By integrating advanced network segmentation and continuous dynamic policy, our solution secures data environments and simplifies compliance, providing a robust foundation for protecting sensitive payment information.
Network microsegmentation is a security concept that involves dividing a computer network into smaller, distinct segments, each with its own unique set of security policies. This approach provides a refined method of controlling access to sensitive areas of the network, such as those containing cardholder data environments (CDE). By applying microsegmentation, organizations can limit an attacker’s ability to move laterally within the network, thereby enhancing the overall security posture and compliance with PCI DSS 4.0.
Under PCI DSS 4.0, microsegmentation becomes an even more critical component, particularly due to the requirements around segmentation and penetration testing:
-
Defined Approach Requirements (Requirement 11.4.5): If segmentation is used to isolate the CDE from other networks, penetration tests are performed on segmentation controls. This involves confirming that segmentation controls are operational and effective, and that they isolate the CDE from all out-of-scope systems.
-
Testing Procedures: Assessors are required to examine segmentation controls and the associated penetration-testing methodology to ensure all segmentation methods are effectively tested (11.4.5.a), to verify the results from the most recent penetration test (11.4.5.b), and to interview personnel to confirm the test was performed by a qualified internal or external third party (11.4.5.c).
-
Guidance and Good Practice: The guidance emphasizes the purpose of segmentation controls to isolate the CDE and highlights good practices such as host discovery and port scanning to verify out-of-scope segments have no access to the CDE.
Elisity’s platform supports these requirements by enabling precise control over traffic to and from the CDE. With its capability to enforce policy-driven segmentation, Elisity’s solution can be assessed for effectiveness in line with the PCI DSS 4.0 standards, which stipulate regular technical testing to ensure continuous efficacy in isolating the CDE.
Incorporating Elisity’s microsegmentation into your security framework not only aligns with PCI DSS 4.0 compliance but also strengthens your organization's ability to protect against breaches and unauthorized data access. Below is an outline of the requirements and testing procedures that highlight the importance of segmentation in maintaining robust security controls:
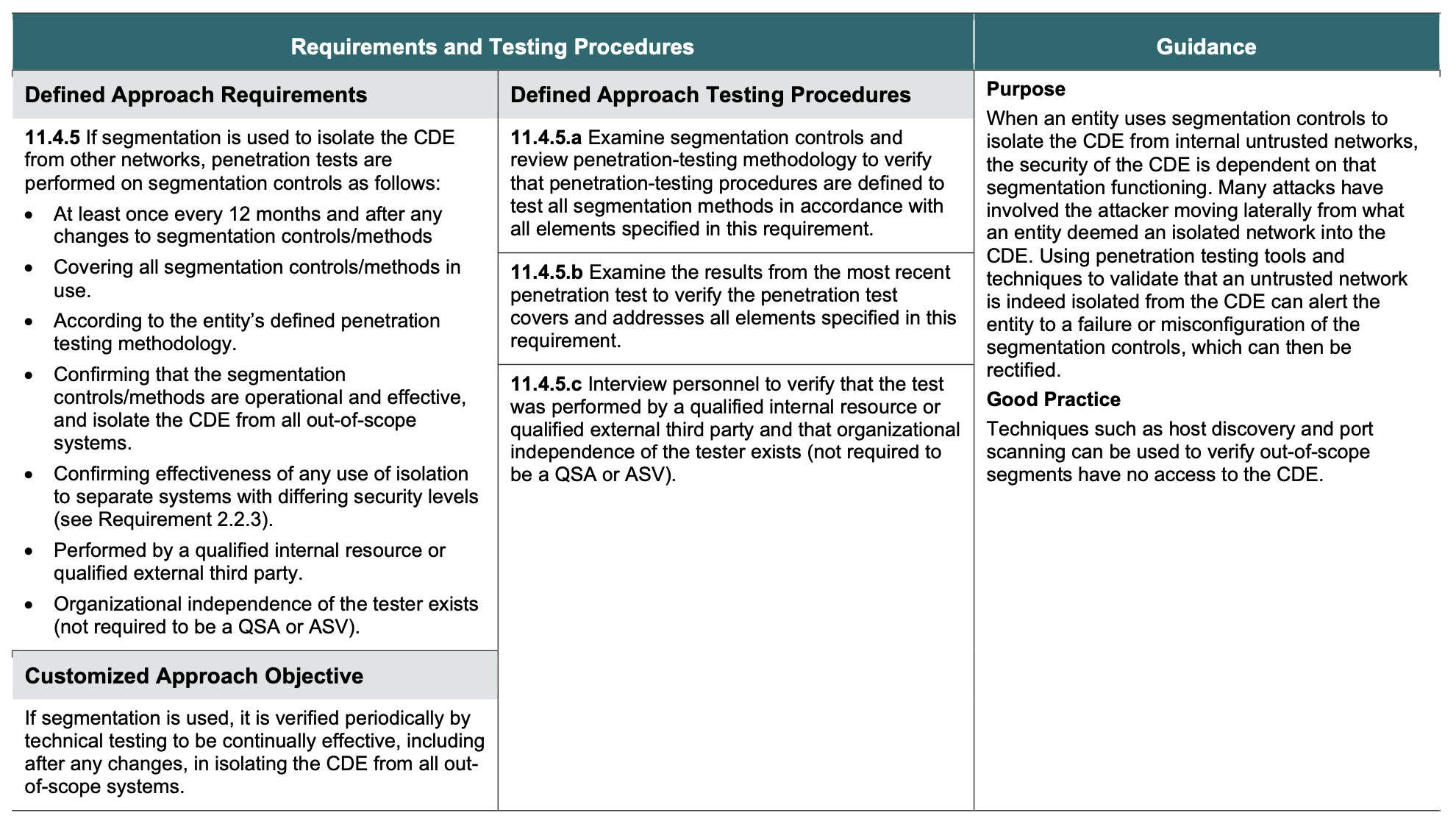
By integrating Elisity’s microsegmentation into your network, you not only meet the defined approach requirements but also leverage a solution that facilitates the necessary testing procedures, aligning with the overall purpose and good practices recommended by PCI DSS 4.0.
Explore our comprehensive PCI DSS 4.0 Compliance documentation. and supplemental Guidance for PCI DSS Scoping and Network Segmentation
Understanding the Scope of Compliance
The Payment Card Industry Data Security Standard (PCI DSS) outlines the necessity to safeguard cardholder data by establishing a cardholder data environment (CDE) that is secure and compliant. Elisity’s microsegmentation capabilities can effectively reduce the scope of this environment by isolating the systems that interact with or impact the security of cardholder data (CHD).
Our updated solutions are at the forefront of compliance innovation, offering unmatched support for the new control objectives under PCI DSS 4.0. Elisity's microsegmentation facilitates enhanced monitoring capabilities and state-of-the-art security protocols, crucial for adhering to the latest regulatory requirements and safeguarding cardholder data against emerging threats.
Elisity’s Role in Reducing Scope
Elisity’s microsegmentation approach focuses on minimizing the number of system components that fall within the CDE. By creating secure and isolated segments within the network, only the systems that need to store, process, or transmit CHD, or that can affect the security of the CDE, are included within the compliance scope. This targeted isolation aligns with the guidance provided in the PCI DSS Scoping and Segmentation document, ensuring that out-of-scope systems cannot impact the security of the CDE.
Benefits of Scope Reduction with Elisity
Reducing the compliance scope offers several benefits:
- Enhanced Security: By narrowing down the focus to a more manageable environment, Elisity helps organizations strengthen their security posture.
- Cost Savings: With fewer systems to protect and monitor, organizations can save on the resources typically allocated for PCI DSS compliance.
- Simplified Compliance: A smaller scope translates to a more straightforward compliance process, making it easier for entities to meet PCI DSS requirements.
- Customized Control: Elisity’s microsegmentation allows for a tailored implementation of controls, providing entities with solutions that specifically address their unique network architectures and business needs.
Continuous Verification and Testing
Elisity’s solution facilitates the ongoing verification and validation of segmentation controls, as mandated by PCI DSS. This involves regular penetration testing and assessment to ensure the effectiveness of segmentation, which is crucial for maintaining PCI DSS compliance.
Elisity’s IdentityGraph™ serves as a continuous, dynamic identity engine. As assets evolve and network dynamics change, the service continually updates its data repository. This ensures that the identity information remains current, and any changes or anomalies are rapidly identified and reconciled. Whether it's a software update on a device, a change in its operational status, or a new device entering the network, IdentityGraph™ ensures that its data remains a reflection of the network's current state.
Learn more about the Elisity IdentityGraph™
Utilizing Elisity’s Microsegmentation
Entities can leverage Elisity’s expertise to design a segmentation strategy that effectively reduces compliance scope while aligning with PCI DSS 4.0 requirements. Through Elisity’s microsegmentation, entities can ensure that their network architecture is not only compliant but also optimized for security and operational efficiency.
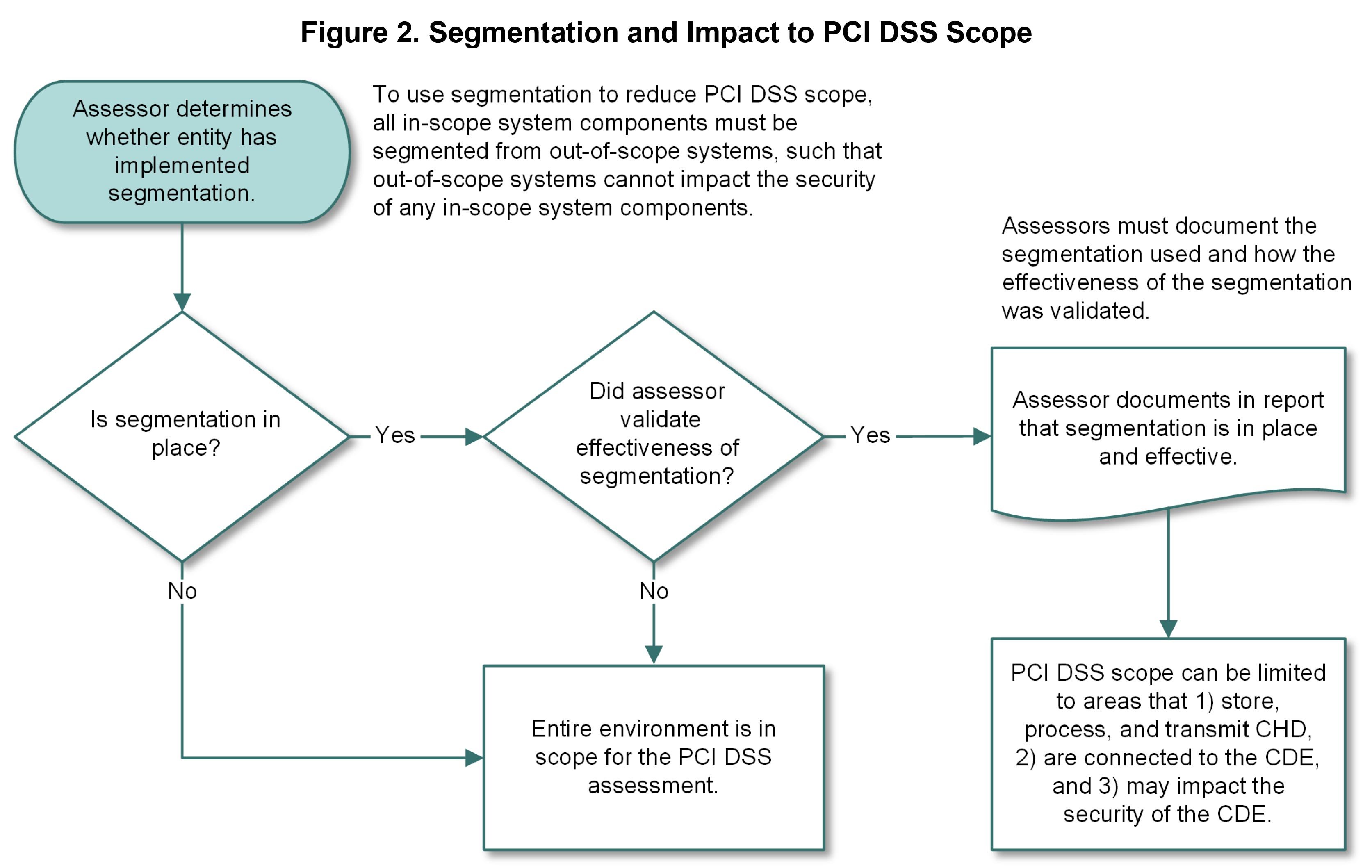
For more detailed guidance on segmentation and its impact on PCI DSS scope, refer to the "PCI DSS Scoping and Segmentation" document.
By strategically applying Elisity’s microsegmentation solutions, organizations can effectively reduce their PCI DSS compliance scope, streamline their security practices, and maintain a robust defense against potential data breaches.
Elisity’s microsegmentation greatly enhances security by leveraging Device Labels and Dynamic Policy Groups, which incorporate identity attributes to create and enforce distinct zones within an organization’s network. This is particularly relevant for securing the Cardholder Data Environment (CDE) and Shared Services, as it allows for the creation of specific allow/deny flows between these zones and ensures complete segmentation from the rest of the corporate LAN.
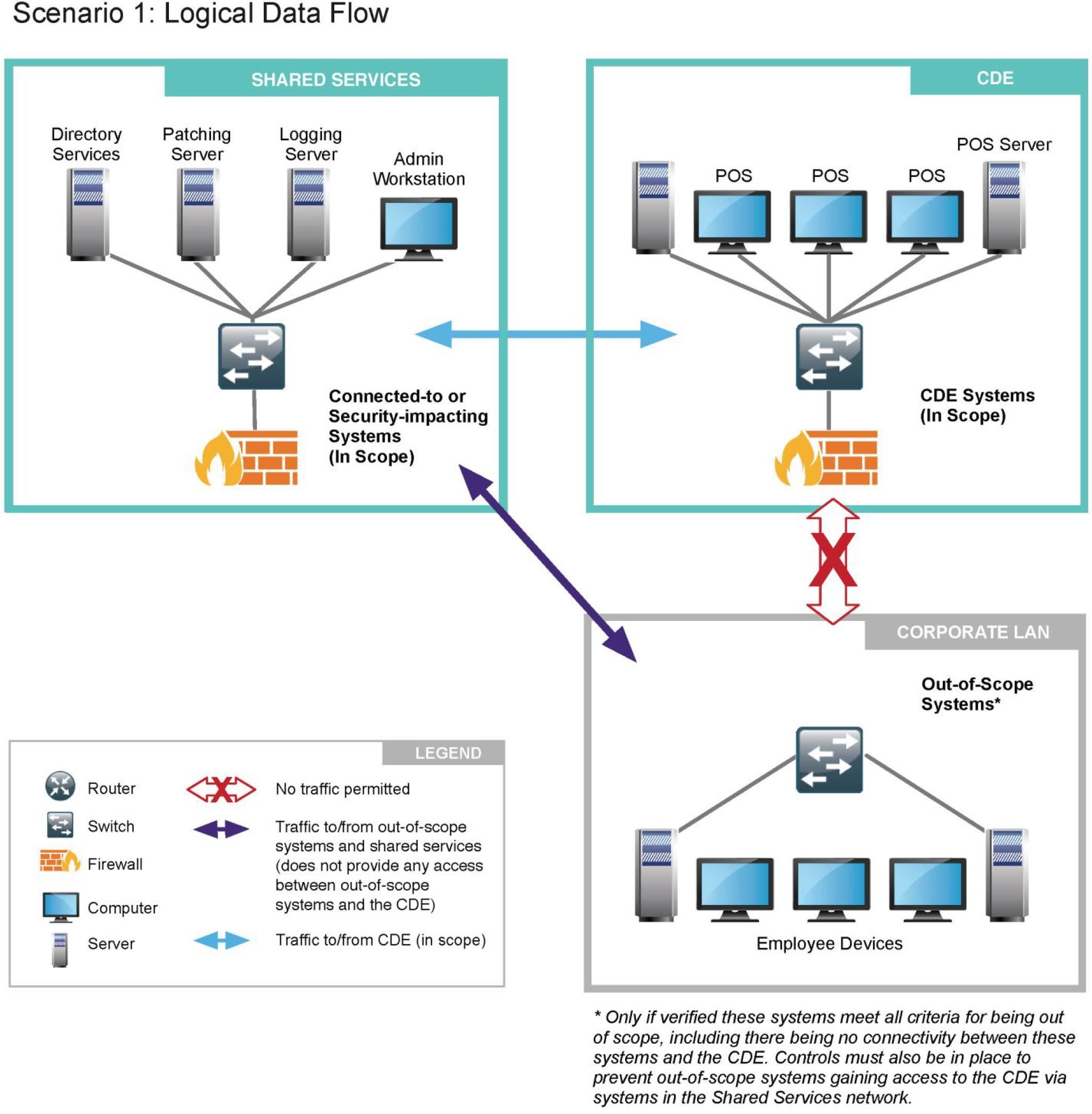
Utilization of Device Labels: With Elisity’s Device Labels, the network administrator can tag devices with specific labels that reflect their role, function, or location. For instance, all devices that are part of the CDE can be labeled accordingly, making it easier to apply consistent security policies across all such devices. Device Labels streamline the application of security controls by associating them with the identity of the devices rather than just their IP addresses.
Learn more about Device Labels
Dynamic Policy Groups: Dynamic Policy Groups in Elisity take this a step further by grouping devices based on identity attributes, such as device type or vendor. These groups can then be used to enforce policies that govern the interactions between the CDE, Shared Services, and other parts of the network. For example, a policy group might be created for all point-of-sale (POS) systems within the CDE, allowing strict control over their communication with payment servers and other critical systems.
Learn more about Policy Groups
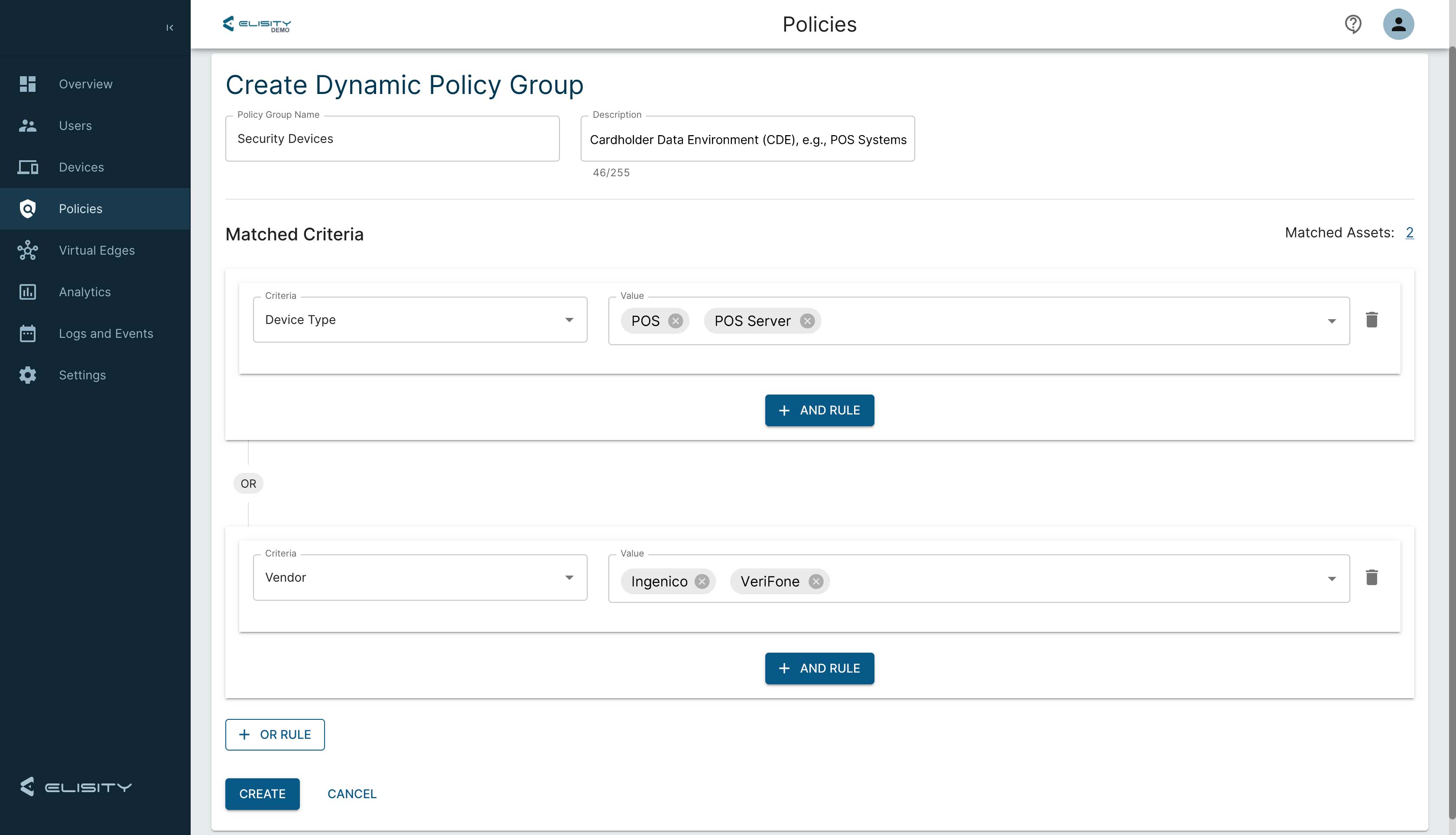
Enforcement of Segmentation Controls: In the PCI DSS scenario, Elisity’s segmentation controls can be aligned to the requirements, ensuring that the CDE is isolated from Shared Services, which in turn are segmented from the Corporate LAN. The Elisity platform facilitates the enforcement of these controls, as seen in the Logical Data Flow diagram from the PCI documentation, by managing the allow and deny network flows based on the defined policy groups.
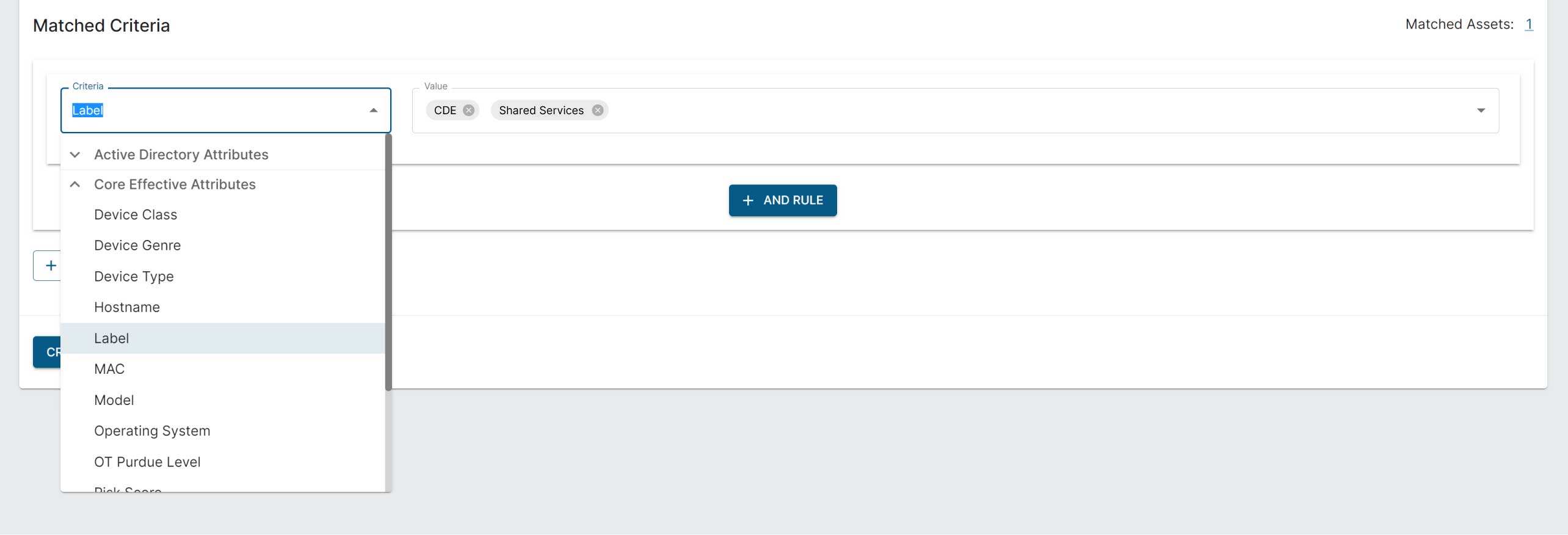
Elisity Platform Interface: The Elisity platform interface exemplifies the ease with which administrators can create these dynamic policy groups. In the provided screenshot, we see the policy creation interface where security devices such as IP cameras and doorbells can be easily managed. Such granular control is essential in maintaining a secure and compliant network environment.
In essence, Elisity’s microsegmentation not only supports PCI DSS 4.0 compliance by enhancing security through identity-based access controls but also simplifies the management of network flows, ensuring that each part of the network is adequately secured and isolated as per the compliance requirements. The use of Device Labels and Dynamic Policy Groups is central to this approach, providing a powerful method for defining and enforcing the necessary segmentation within the network.
Explore our comprehensive PCI DSS 4.0 Compliance documentation. and supplemental Guidance for PCI DSS Scoping and Network Segmentation
Elisity’s microsegmentation capabilities are designed to align with the Payment Card Industry Data Security Standard (PCI DSS) 4.0, particularly in the context of network segmentation. Network segmentation is a critical aspect of PCI DSS that helps reduce the scope of the cardholder data environment (CDE), minimize risk, and simplify compliance efforts. While not explicitly required by the PCI DSS, segmentation is strongly recommended and widely recognized as a best practice for securing cardholder data.
Elisity’s approach to microsegmentation adheres to the segmentation requirements outlined in PCI DSS 4.0 by ensuring that only authorized systems and users have access to the CDE. This is achieved through purpose-built controls that create and enforce strict separation between the CDE and out-of-scope systems. The Elisity platform leverages identity-based microsegmentation, which goes beyond traditional IP address-based controls, allowing for more granular and dynamic security policies that are tied to user and device identities.
Key points of alignment include:
-
Enforcement of Separation: Elisity ensures that systems within the CDE are isolated from those that do not store, process, or transmit cardholder data. This isolation is critical for reducing PCI DSS scope and is a cornerstone of PCI DSS's segmentation principles.
-
Purpose-Built Controls: Elisity’s platform employs segmentation controls that are specifically designed to limit communications between the CDE and other networks, as recommended by PCI DSS guidelines. These controls include firewalls and access control lists that are configured to prevent any unauthorized access.
-
Annual Verification and Testing: As per PCI DSS requirements, Elisity supports the annual verification and testing of segmentation controls to ensure they remain effective. This is crucial for maintaining the integrity of the CDE's isolation.
-
Reduction of CDE Scope: By effectively segmenting the network, Elisity helps organizations minimize their CDE scope, which in turn reduces the number of systems that need to comply with PCI DSS requirements, as well as the associated costs and complexities of maintaining compliance.
-
Customized Implementation: Elisity’s microsegmentation solutions can be tailored to meet the specific requirements of an organization, ensuring that PCI DSS controls are implemented in a manner that aligns with the entity's unique environment and business needs.
-
Continuous Compliance: Elisity facilitates continuous monitoring and enforcement of segmentation controls, which aligns with PCI DSS's requirement for ongoing security.

Elisity’s microsegmentation is not only compatible with PCI DSS 4.0 segmentation requirements but also enhances the security posture by providing a more adaptive and identity-aware approach to isolating the CDE. This results in a robust compliance framework that is designed to evolve with an organization’s needs and the ever-changing security landscape.
For a detailed understanding of PCI DSS scoping and segmentation, readers can refer to the supplemental guidance provided by the PCI Security Standards Council, specifically the document "Guidance for PCI DSS Scoping and Network Segmentation". Furthermore, for comprehensive insights into all PCI DSS 4.0 requirements, the complete document "PCI DSS v4.0" is available for reference.
Explore our comprehensive PCI DSS 4.0 Compliance documentation. and supplemental Guidance for PCI DSS Scoping and Network Segmentation
Customization is key to aligning security solutions with specific organizational needs, and Elisity’s microsegmentation is no exception when it comes to adherence to PCI DSS 4.0. This standard introduces robust requirements for segmentation, ensuring that only necessary systems are within the Cardholder Data Environment (CDE) to minimize risk and maintain compliance. Elisity’s microsegmentation can be tailored to meet these stringent requirements, offering a powerful tool for enhancing your organization's security posture while aligning with PCI DSS 4.0 mandates.
- Customized Control Implementation: Elisity’s solutions are designed with flexibility in mind, allowing your organization to implement microsegmentation controls that are customized to your unique environment. This capability is particularly important as PCI DSS 4.0 does not permit a one-size-fits-all approach and expects entities to reflect their specific risk scenarios and control needs.
- Alignment with Specific PCI DSS 4.0 Requirements: By utilizing Elisity’s microsegmentation capabilities, your organization can align with specific PCI DSS 4.0 requirements. For instance, Elisity’s approach can ensure that your CDE is properly segmented from out-of-scope systems and that segmentation controls are tested and verified, meeting the requirement for maintaining a documented and validated scope as per PCI DSS 4.0, Appendix A3.2.4.
- Support for Continuous Compliance: Elisity’s microsegmentation facilitates continuous compliance monitoring, a cornerstone of PCI DSS 4.0. This ongoing process ensures that your organization remains compliant with the standard's requirements, such as the regular review of hardware and software technologies to confirm they continue to meet PCI DSS standards, as mentioned in PCI DSS 4.0, Appendix A3.3.2.
- Assessment and Adjustment: Adaptation is a continuous process. Elisity supports periodic reassessment of microsegmentation configurations to ensure they remain effective and compliant with the latest PCI DSS version. This practice aligns with PCI DSS 4.0’s emphasis on regular validation of the scope and effectiveness of segmentation controls.
The flexibility of Elisity’s microsegmentation provides your organization with the tools necessary to tailor your network segmentation in compliance with PCI DSS 4.0. This customized approach not only meets compliance requirements but also fortifies your security measures by limiting potential exposure points within your network infrastructure.
Explore our comprehensive PCI DSS 4.0 Compliance documentation. and supplemental Guidance for PCI DSS Scoping and Network Segmentation
In PCI DSS 4.0, continuous compliance is emphasized to ensure that security controls and processes are not only implemented but also maintained effectively and consistently as part of the business-as-usual (BAU) activities. PCI DSS 4.0 mandates the implementation of a PCI DSS compliance program that is robust, well-documented, and validated. This program is required to incorporate the following elements:
-
PCI DSS Compliance Program: This is a formal structure within an organization that ensures PCI DSS controls are maintained effectively and continuously. It establishes clear accountability and includes periodic assessments to validate compliance.
-
Documentation and Validation of PCI DSS Scope: Organizations must confirm the accuracy of their PCI DSS scope regularly, at least once every three months, and whenever significant changes occur. This involves identifying all data flows, locations of account data, and all system components in the CDE, as well as verifying that segmentation controls are operational and effective.
-
Incorporation into Business-As-Usual Activities: PCI DSS requirements must be integrated into the daily operations of the organization. This ensures that maintaining PCI DSS compliance becomes a part of the culture and operating procedures of the entity.
-
Controlled and Managed Access to the CDE: Logical access to the cardholder data environment must be strictly controlled and managed, ensuring that only authorized individuals have access to sensitive data.
-
Identification and Response to Suspicious Events: Organizations must have processes in place to detect and respond to suspicious events promptly to prevent or mitigate security breaches.
Elisity supports continuous compliance in PCI DSS 4.0 by providing a framework that aligns with these requirements. Elisity's capabilities in microsegmentation and identity-based policies ensure that access to the CDE is tightly controlled, reducing the risk of unauthorized access. Elisity's dynamic policy groups can be used to enforce segmentation policies, thereby supporting the maintenance of PCI DSS scope as defined by the entity's specific requirements. Additionally, Elisity's analytics and continuous monitoring capabilities can help identify and respond to suspicious events, thereby maintaining the security posture required for PCI DSS compliance on an ongoing basis.
Explore our comprehensive PCI DSS 4.0 Compliance documentation. and supplemental Guidance for PCI DSS Scoping and Network Segmentation
Assessors play a crucial role in evaluating the effectiveness of network segmentation for PCI DSS compliance. Their main tasks involve:
-
Validation of Documentation: Assessors are required to validate that the scope of the PCI DSS assessment is accurately defined and documented. This includes a review of the assessed entity’s documentation to confirm the scope is properly outlined and segmented as per the PCI DSS requirements.
-
Scope Accuracy Confirmation: While the responsibility to determine and confirm the accuracy of PCI DSS scope annually lies with the entity itself, assessors must verify that the entity has accurately defined and documented this scope. Assessors are expected to question any unclear scoping decisions and work collaboratively with the entity to understand the decisions made regarding scope definition.
-
Verification of Segmentation Controls: When network segmentation is used to reduce the PCI DSS assessment scope, assessors must check that the segmentation is adequate. This means that the controls in place effectively isolate the cardholder data environment (CDE) from out-of-scope systems and prevent potential security breaches from out-of-scope systems reaching the CDE.
-
Annual Penetration Testing: To ensure the continued effectiveness of segmentation controls, they must be subject to penetration testing at least annually. This testing confirms that the segmentation controls are robust and that there are no vulnerabilities that could be exploited to compromise the CDE.
Through these processes, assessors ensure that entities not only claim but also demonstrate the effective implementation of network segmentation, which is a vital component of maintaining PCI DSS compliance.

Explore our comprehensive PCI DSS 4.0 Compliance documentation. and supplemental Guidance for PCI DSS Scoping and Network Segmentation
Payment and Billing
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Donec quam felis, ultricies nec, pellentesque eu, pretium quis, sem. Nulla consequat massa quis enim. Donec pede justo, fringilla vel, aliquet nec, vulputate eget, arcu. In enim justo, rhoncus ut, imperdiet a, venenatis vitae, justo. Nullam dictum felis eu pede mollis pretium. Integer tincidunt. Cras dapibus. Vivamus elementum semper nisi.
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Donec quam felis, ultricies nec, pellentesque eu, pretium quis, sem. Nulla consequat massa quis enim. Donec pede justo, fringilla vel, aliquet nec, vulputate eget, arcu. In enim justo, rhoncus ut, imperdiet a, venenatis vitae, justo. Nullam dictum felis eu pede mollis pretium. Integer tincidunt. Cras dapibus. Vivamus elementum semper nisi.
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Donec quam felis, ultricies nec, pellentesque eu, pretium quis, sem. Nulla consequat massa quis enim. Donec pede justo, fringilla vel, aliquet nec, vulputate eget, arcu. In enim justo, rhoncus ut, imperdiet a, venenatis vitae, justo. Nullam dictum felis eu pede mollis pretium. Integer tincidunt. Cras dapibus. Vivamus elementum semper nisi.
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Donec quam felis, ultricies nec, pellentesque eu, pretium quis, sem. Nulla consequat massa quis enim. Donec pede justo, fringilla vel, aliquet nec, vulputate eget, arcu. In enim justo, rhoncus ut, imperdiet a, venenatis vitae, justo. Nullam dictum felis eu pede mollis pretium. Integer tincidunt. Cras dapibus. Vivamus elementum semper nisi.
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Donec quam felis, ultricies nec, pellentesque eu, pretium quis, sem. Nulla consequat massa quis enim. Donec pede justo, fringilla vel, aliquet nec, vulputate eget, arcu. In enim justo, rhoncus ut, imperdiet a, venenatis vitae, justo. Nullam dictum felis eu pede mollis pretium. Integer tincidunt. Cras dapibus. Vivamus elementum semper nisi.
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Donec quam felis, ultricies nec, pellentesque eu, pretium quis, sem. Nulla consequat massa quis enim. Donec pede justo, fringilla vel, aliquet nec, vulputate eget, arcu. In enim justo, rhoncus ut, imperdiet a, venenatis vitae, justo. Nullam dictum felis eu pede mollis pretium. Integer tincidunt. Cras dapibus. Vivamus elementum semper nisi.
Getting Started
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Donec quam felis, ultricies nec, pellentesque eu, pretium quis, sem. Nulla consequat massa quis enim. Donec pede justo, fringilla vel, aliquet nec, vulputate eget, arcu. In enim justo, rhoncus ut, imperdiet a, venenatis vitae, justo. Nullam dictum felis eu pede mollis pretium. Integer tincidunt. Cras dapibus. Vivamus elementum semper nisi.
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Donec quam felis, ultricies nec, pellentesque eu, pretium quis, sem. Nulla consequat massa quis enim. Donec pede justo, fringilla vel, aliquet nec, vulputate eget, arcu. In enim justo, rhoncus ut, imperdiet a, venenatis vitae, justo. Nullam dictum felis eu pede mollis pretium. Integer tincidunt. Cras dapibus. Vivamus elementum semper nisi.
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Donec quam felis, ultricies nec, pellentesque eu, pretium quis, sem. Nulla consequat massa quis enim. Donec pede justo, fringilla vel, aliquet nec, vulputate eget, arcu. In enim justo, rhoncus ut, imperdiet a, venenatis vitae, justo. Nullam dictum felis eu pede mollis pretium. Integer tincidunt. Cras dapibus. Vivamus elementum semper nisi.
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Donec quam felis, ultricies nec, pellentesque eu, pretium quis, sem. Nulla consequat massa quis enim. Donec pede justo, fringilla vel, aliquet nec, vulputate eget, arcu. In enim justo, rhoncus ut, imperdiet a, venenatis vitae, justo. Nullam dictum felis eu pede mollis pretium. Integer tincidunt. Cras dapibus. Vivamus elementum semper nisi.
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Donec quam felis, ultricies nec, pellentesque eu, pretium quis, sem. Nulla consequat massa quis enim. Donec pede justo, fringilla vel, aliquet nec, vulputate eget, arcu. In enim justo, rhoncus ut, imperdiet a, venenatis vitae, justo. Nullam dictum felis eu pede mollis pretium. Integer tincidunt. Cras dapibus. Vivamus elementum semper nisi.
Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aenean commodo ligula eget dolor. Aenean massa. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Donec quam felis, ultricies nec, pellentesque eu, pretium quis, sem. Nulla consequat massa quis enim. Donec pede justo, fringilla vel, aliquet nec, vulputate eget, arcu. In enim justo, rhoncus ut, imperdiet a, venenatis vitae, justo. Nullam dictum felis eu pede mollis pretium. Integer tincidunt. Cras dapibus. Vivamus elementum semper nisi.






