Redefining Unidirectional Gateways: The Shift from Hardware to Software
Elisity’s Innovative Approach to Data Diodes: Flexibility, Scalability, and Advanced Security in Modern OT Networks
Introduction
In the age of digital transformation, ensuring the security of data flow within and between networks has become paramount. Data diodes, or unidirectional gateways, have emerged as a trusted solution to this challenge, providing a one-way data transfer mechanism that safeguards critical information. This paper delves into the essence of data diodes, their applications, and the limitations of conventional hardware-based solutions. We then introduce Elisity’s innovative software-based approach, highlighting its superior flexibility, scalability, cost-effectiveness, and advanced features.
Download this White Paper
Understanding Data Diodes
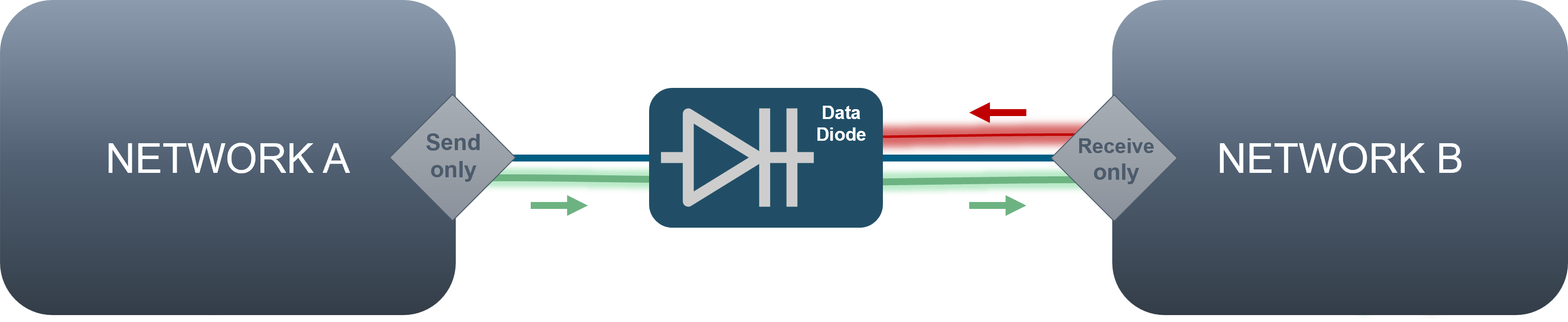
A data diode is a unidirectional network communication device designed to facilitate the safe, one-way transfer of data between segmented networks. By maintaining a physical and electrical separation between source and destination networks, data diodes eliminate potential external entry points to the sending system. This ensures that threats like malware cannot infiltrate the network, and unauthorized changes are prevented. Such a mechanism is invaluable for companies aiming to transmit real-time process data to management systems without compromising network security.
Download this Solution Brief
Who Benefits from Data Diodes?

From critical infrastructure operators to defense industries, data diodes have found a place in a myriad of sectors. Their application is not limited to high-security environments; even commercial entities like financial institutions leverage them. For instance, power generation facilities use data diodes to protect critical equipment, allowing data to flow out seamlessly while blocking any external access.
The Expanding Need for Data Diodes
With the rise of digitalization and sophisticated cyberattacks, the need for data diodes extends beyond traditional sectors. Any organization handling sensitive information can benefit from the protection offered by data diodes, ensuring the integrity and availability of their systems.
Data diodes can be directed either out from a high-security network or towards it. Their versatility allows for a plethora of applications, including:
- IoT sensor networks
- HTTP mirrors
- Traffic tapping
- Video streaming
- Logging
Limitations of Conventional Data Diodes
While data diodes have been a cornerstone in ensuring one-way data transfer for security purposes, conventional hardware-based solutions present several challenges:
- Inflexibility: Traditional hardware-based data diodes are rigid in their design and deployment. Implementing or updating these solutions often necessitates significant infrastructure changes. This rigidity translates to potential network downtime whenever a new data diode is deployed or when there’s a need to modify the traffic being enforced.
- Scalability Issues: As organizations expand and their data requirements grow, hardware solutions can quickly become bottlenecks. This means operators have to ensure their chosen hardware can support the performance demands of the network. They must also be prepared to upgrade these systems when they become insufficient. Furthermore, the need to constantly monitor these systems for peak efficiency, design for high availability, and plan for fail scenarios adds layers of complexity. The deployment of a new data diode for every new network zone that requires unidirectional traffic enforcement can become an operational burden.
- High Costs: The financial implications of hardware solutions are twofold. Firstly, there’s a high initial cost associated with their purchase. Secondly, organizations may incur additional expenses during upgrades or replacements, making them less cost-effective in the long run.
- Limited Features: Conventional data diodes often come with a restricted set of features. They might not support advanced functionalities like detailed logging, analytics, or seamless integration with other security tools, limiting their utility in dynamic and evolving network environments.
The Elisity Advantage: A Software-Based Revolution
Elisity’s innovative software approach to unidirectional traffic control and enforcement offers a plethora of advantages over traditional data diodes:
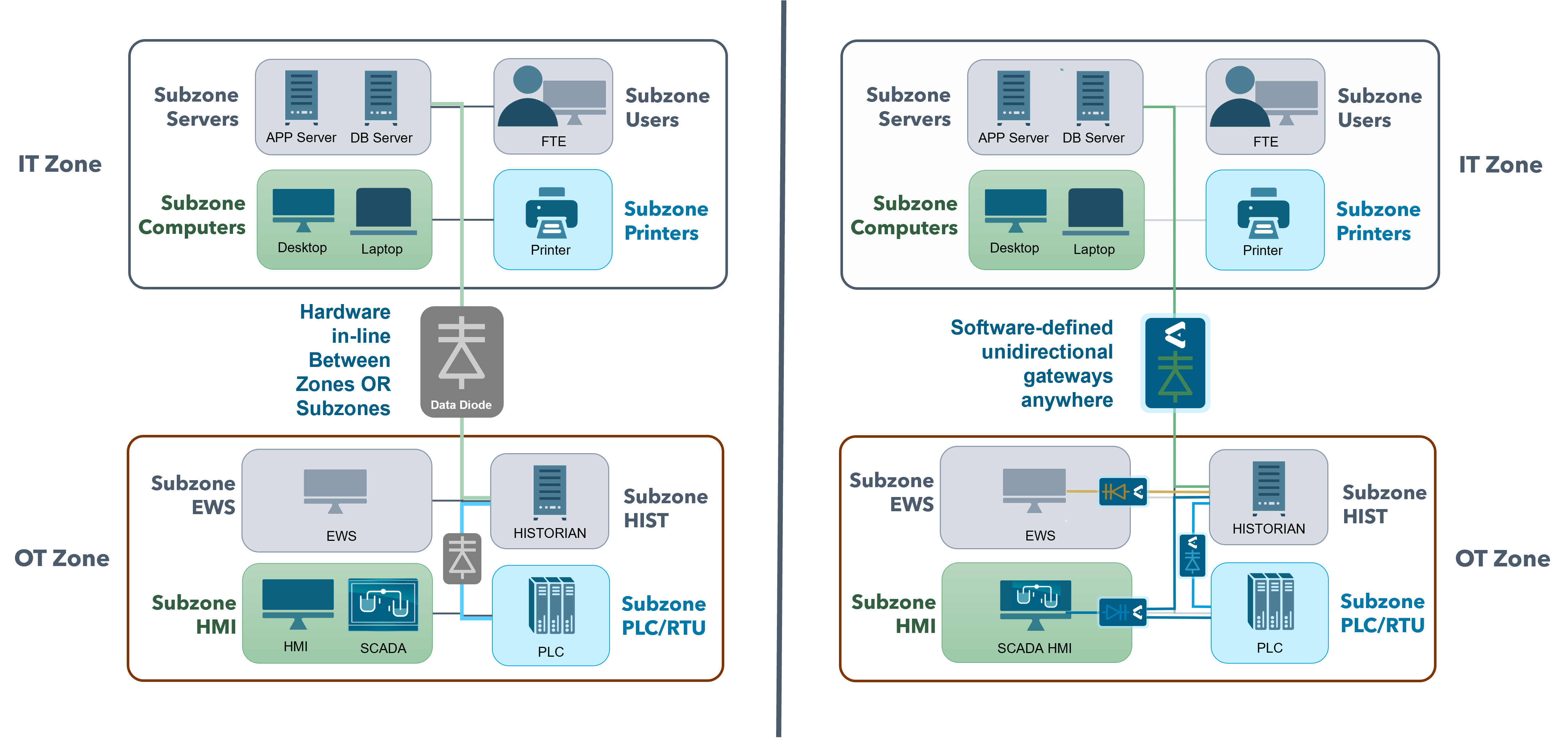
- Flexibility: Unlike their hardware counterparts, Elisity’s software solutions are inherently flexible. They can be easily deployed, modified, or scaled without the need for extensive hardware changes. This solution transforms existing access network infrastructure into dynamic unidirectional enforcement points that can be activated within minutes. Even if there are changes to an environment’s physical network, zones, or conduit requirements, Elisity’s software can be reprogrammed to adapt with zero packet loss, ensuring uninterrupted service.
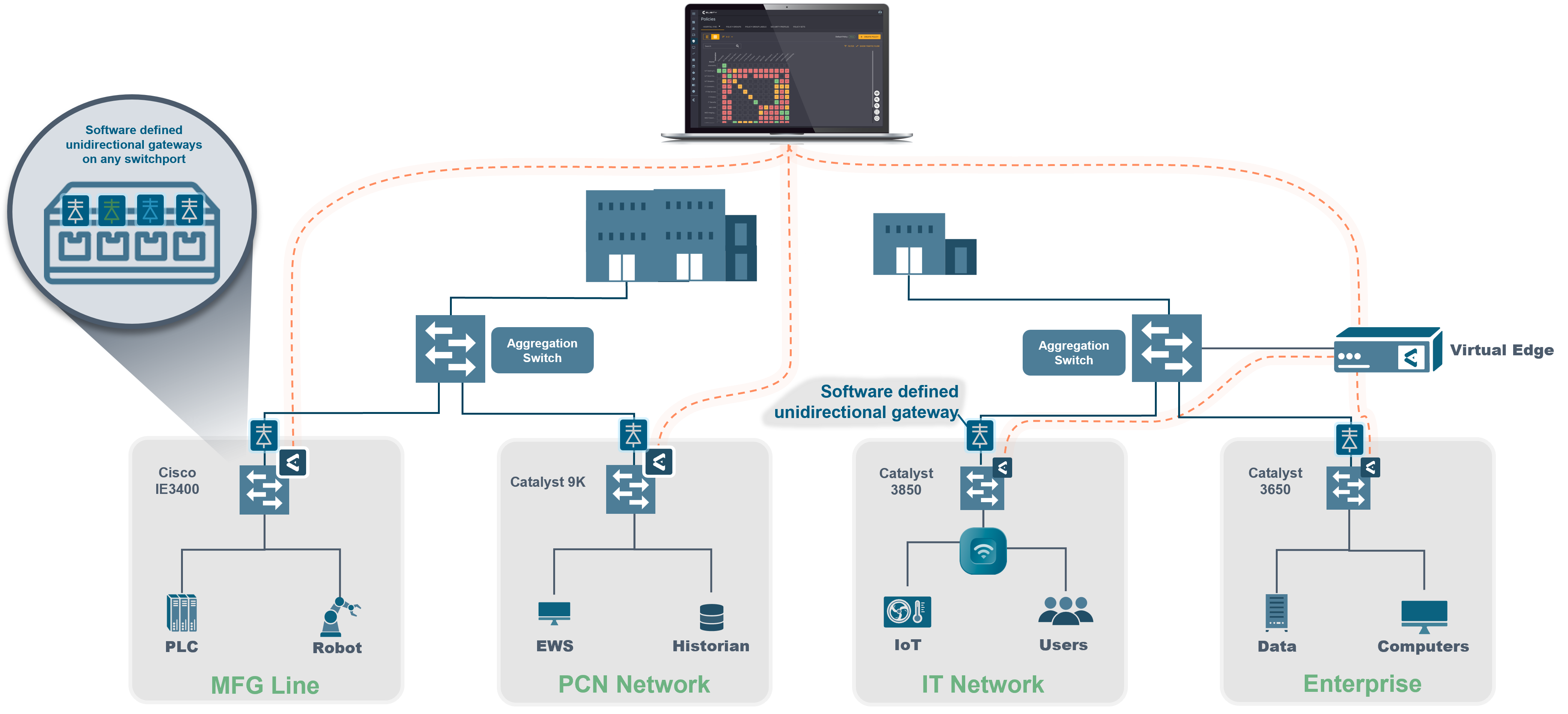
- Enhanced Scalability: Elisity’s approach is designed for growth. By leveraging existing access network infrastructure and being entirely software-based, unidirectional enforcement can be deployed anywhere on the network without performance or scale limitations. This eliminates the operational burden of managing multiple physical appliances. Instead, organizations benefit from a single unified management console to oversee all policies deployed across the entire domain. Additionally, high availability is built into the solution, further leveraging the high performance and reliability of existing industrial or corporate networks.
- Cost-Effective: The software-based nature of Elisity’s solution eliminates the need for frequent hardware upgrades or replacements. This not only reduces initial costs but also ensures that the solution remains more cost-effective over its lifecycle.
- Advanced Features: Elisity’s software-based approach is feature-rich. It offers dynamic device detection and profiling using IdentityGraph™, detailed logging, analytics, and seamless integration with other security tools. Additionally, it provides dynamic edge segmentation based on the identity and attributes of devices, users, and applications. This ensures organizations can easily meet ICS cybersecurity standards, such as IEC62443, especially concerning segmentation.
Navigating Towards a Secure Future: The Elisity Advantage
Unidirectional gateways or data diodes play a crucial role in cybersecurity, ensuring that sensitive data remains protected from potential threats. While conventional hardware-based data diodes have served their purpose, the modern challenges of cybersecurity require more adaptable, scalable, and feature-rich solutions. Elisity’s software-based approach to unidirectional traffic control and enforcement is a testament to the evolution of cybersecurity tools, offering organizations a more efficient, flexible, and cost-effective solution.
Download this Solution Brief
From Our Blog
Stay up to date with what is new in our industry, learn more about the upcoming products and events.

Top Healthcare Cybersecurity Vendors for 2026 [Compared]

Living Off the Land Attacks in OT: The Microsegmentation Fix




