Share this
CISA Microsegmentation in Zero Trust, Part One: Introduction and Planning - How Elisity Makes It Actionable
by William Toll on Aug 5, 2025 11:11:24 AM
When CISA released Microsegmentation in Zero Trust, Part One: Introduction and Planning on July 29, 2025, security leaders across industries received validation for what many already knew: microsegmentation has evolved from a nice-to-have security control into a fundamental requirement for protecting modern networks. But while CISA's guidance provides the strategic framework, organizations still face the daunting question of execution—how do you actually implement these recommendations without derailing operations or breaking the budget?
The answer lies in understanding both the evolution of Zero Trust principles and the practical realities of implementation. More specifically, it requires a solution that transforms CISA's theoretical guidance into operational reality within weeks, not years.
Understanding CISA Microsegmentation in Zero Trust, Part One: Introduction and Planning
The new CISA document, Microsegmentation in Zero Trust, Part One: Introduction and Planning, represents a significant milestone in federal cybersecurity guidance. While previous Zero Trust frameworks provided high-level principles, this specific guidance offers actionable steps for organizations ready to implement microsegmentation as a core Zero Trust control.
The Long Road to Zero Trust Maturity
Zero Trust has been a cornerstone of cybersecurity discussions since John Kindervag coined the term at Forrester Research in 2010. The concept challenged the traditional castle-and-moat security model where everything inside the network perimeter was trusted by default. Instead, Zero Trust operates on a simple principle: never trust, always verify.
NIST formalized these concepts in Special Publication 800-207
, defining Zero Trust Architecture (ZTA) as a collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions. The framework established core tenets including continuous verification, limiting the blast radius of breaches, and automating context collection and response.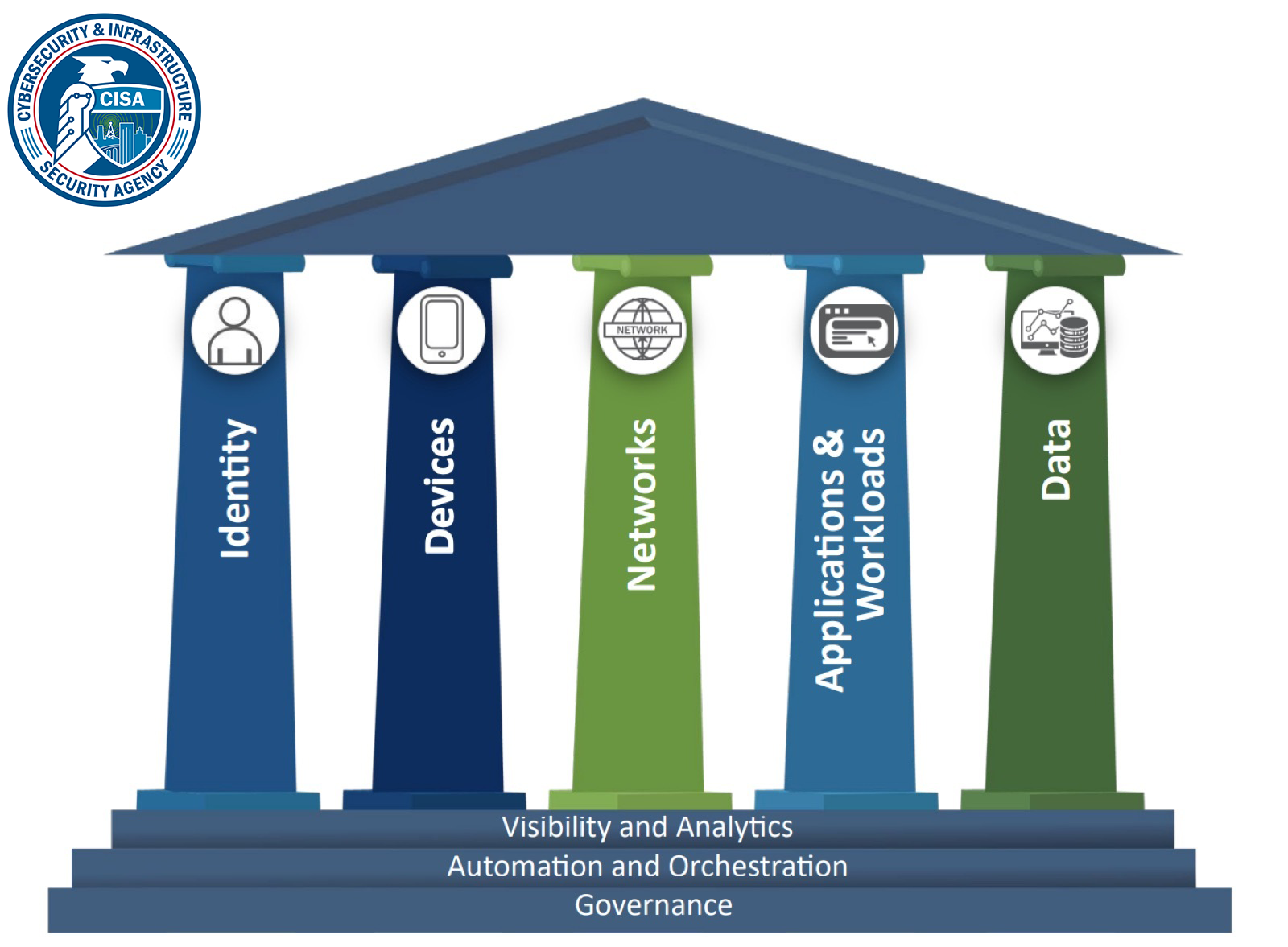
CISA Zero Trust Maturity Model - Network
Yet despite widespread acceptance of Zero Trust principles, implementation has remained elusive for most organizations. Traditional approaches to microsegmentation—involving hundreds of firewall rules, VLAN reconfigurations, and agent deployments—turned what should be security improvements into multi-year infrastructure overhauls. A pharmaceutical company planning traditional firewall-based segmentation across 275 sites calculated it would take one year per location and $200 million to complete. Healthcare systems faced similar challenges, with one major health system estimating they'd need 14 employees and 300 hours per site just to implement basic segmentation.
These implementation barriers created a dangerous gap between security theory and practice. While CISOs understood the need to limit lateral movement (the tactic used in over 70% of successful breaches), the complexity and cost of traditional solutions left networks vulnerable. This is precisely why CISA's Microsegmentation in Zero Trust, Part One: Introduction and Planning focuses so heavily on phased, practical implementation approaches.
Key Elements of CISA's Microsegmentation in Zero Trust Guidance
CISA's Microsegmentation in Zero Trust, Part One: Introduction and Planning acknowledges these challenges while providing a pragmatic path forward. The document positions microsegmentation not as a network project but as a fundamental shift in how organizations approach security architecture. Several key recommendations from the guidance stand out:
Phased Implementation Over Big Bang Approaches
The CISA Microsegmentation in Zero Trust, Part One: Introduction and Planning document explicitly advocates for incremental adoption, recognizing that organizations cannot simply flip a switch to achieve Zero Trust. The guidance outlines four phases: identifying candidate resources, mapping dependencies, determining appropriate policies, and deploying with validation. This phased approach allows organizations to build expertise and demonstrate value while minimizing disruption.
Dynamic Policy Enforcement Through PEPs
Moving beyond static firewall rules, CISA's new microsegmentation guidance emphasizes Policy Enforcement Points (PEPs) that make real-time decisions based on identity and context. These PEPs don't just check access at connection time—they continuously validate that access remains appropriate throughout the session. If a device's security posture changes or anomalous behavior is detected, policies can adapt automatically.
CISA TIC 2.0 Trusted Internet Connections
Identity-Centric Security Beyond Network Addresses
Perhaps most significantly, the Microsegmentation in Zero Trust, Part One: Introduction and Planning guidance definitively moves microsegmentation beyond IP addresses and VLANs. Modern microsegmentation uses identity attributes—user roles, device types, security postures, behavioral patterns—to make access decisions. A radiology workstation gets consistent policies whether it's in the main hospital or a satellite clinic, because policies follow identity, not location.
Augmenting Existing Infrastructure
CISA recognizes in this guidance that organizations cannot afford to rip and replace their entire network infrastructure. The document emphasizes working with existing investments while adding the intelligence layer needed for Zero Trust. This pragmatic approach acknowledges both budget constraints and the operational reality that networks must continue functioning during the transition.
How Elisity Aligns with CISA Microsegmentation in Zero Trust, Part One
While CISA's Microsegmentation in Zero Trust, Part One: Introduction and Planning provides the "what" and "why" of microsegmentation, Elisity delivers the "how"—and does so with unprecedented speed and simplicity. The alignment between CISA's recommendations and Elisity's capabilities runs deep:
Discovery That Reveals Your True Attack Surface
The CISA guidance emphasizes the importance of identifying all resources before attempting segmentation. Elisity's discovery engine achieves 99% device visibility within hours of deployment, uncovering not just managed IT assets but also the shadow IT, IoT, OT ad IoMT, devices that often provide attack vectors.
Unlike traditional tools that rely on manual asset inventories, Elisity continuously discovers and classifies devices as they appear on the network. The platform's IdentityGraph™ correlates data from your existing tools—Active Directory, CrowdStrike, ServiceNow, specialized IoT security platforms—creating a living inventory that stays current without manual updates.
Aaron Weismann, CISO at Main Line Health, describes the impact: "Elisity's identity-based microsegmentation brings tremendous capabilities to our security stack as a critical control point for containing ransomware, blocking malicious lateral network traffic, and minimizing incident blast radius."
Policy Simulation That Eliminates Fear
CISA's Microsegmentation in Zero Trust, Part One: Introduction and Planning recommends testing policies in "permissive mode" before enforcement—excellent advice that's often easier said than done. Elisity's policy simulation engine shows exactly what traffic would be blocked before you enforce a single rule. The visual Elisity Traffic Flow Matrix displays communication patterns between policy groups, with green indicating allowed traffic and red showing what would be denied.
This simulation capability transformed microsegmentation from a high-risk network change into a controlled, predictable process. Teams can refine policies based on actual traffic patterns, ensuring business operations continue uninterrupted. As one Elisity customer noted, "We were able to create blocking rules and did in fact do that live, and it was really impressive to be able to see from implementation to execution how quickly that could happen."
Dynamic Enforcement Without Infrastructure Overhaul
Where CISA's microsegmentation guidance calls for dynamic, attribute-based policies, Elisity delivers through its cloud-managed Elisity Dynamic Policy Engine. Policies adapt in real-time based on changing contexts—a device showing indicators of compromise can be automatically isolated, while a user accessing sensitive data after hours might face additional restrictions.
Critically, Elisity achieves this without requiring new hardware, agents, or network redesigns. The platform's Virtual Edge software runs on your existing Cisco, Juniper, Aruba, Hirshmann or Arista switches, transforming them into intelligent enforcement points. This approach directly supports the CISA Microsegmentation in Zero Trust, Part One: Introduction and Planning guidance to augment rather than replace existing infrastructure.
Identity-Based Policies That Scale
Traditional segmentation ties policies to network constructs—IP addresses, VLANs, firewall rules—creating brittle configurations that break when networks change. Elisity implements the vision outlined in CISA's guidance through policy groups defined by attributes, not addresses.
Consider a healthcare environment: instead of maintaining separate firewall rules for imaging equipment at each location, Elisity creates a single "Medical Imaging Devices" policy group. Any device matching the profile—whether through Active Directory tags, device fingerprinting, or integration with medical device security tools—automatically receives appropriate policies wherever it connects.
This identity-centric approach dramatically simplifies policy management while improving security. GSK, the global pharmaceutical company, leveraged this capability to implement microsegmentation across 275 sites, reducing their timeline from centuries to months and cutting costs by 75%.
Implementing CISA's Microsegmentation in Zero Trust Guidance: The Acceleration Factor
The CISA Microsegmentation in Zero Trust, Part One: Introduction and Planning document acknowledges that microsegmentation is a journey, but it doesn't address the urgency many organizations face. With ransomware attacks occurring every 11 seconds and regulated industries facing strict compliance deadlines, the difference between implementation in weeks versus years can determine whether an organization leads or merely survives.
Elisity customers consistently report deployment times that seem impossible by traditional standards:
- Main Line Health deployed across hospitals and clinics with just a few full-time employees
- Sites typically go live within 2-8 hours of Elisity Virtual Edge deployment
- First protective policies activate within days, not months
- Full production rollout achieves in weeks what traditional approaches require years to accomplish
>>Watch Aaron Weisman discuss the microsegmentation implementation
at Main Line Health.
This acceleration doesn't sacrifice sophistication for speed. Organizations implementing the CISA microsegmentation guidance with Elisity report:
- 95% reduction in potential attack spread
- 70-90% reduction in attack surface through elimination of unnecessary communications
- Mean-time-to-contain dropping from hours to minutes
- 15-30% reductions in cyber insurance premiums
Continuous Evolution Without Disruption
CISA's Microsegmentation in Zero Trust, Part One: Introduction and Planning emphasizes that Zero Trust is a journey, not a destination. Elisity's cloud-delivered architecture ensures your microsegmentation evolves continuously without disruptive upgrade cycles. New threat intelligence, additional device types, and expanding policy requirements integrate seamlessly into the existing deployment.
The Elisity platform's API-first architecture also supports the dynamic, context-aware security vision outlined in the CISA guidance. When your EDR platform identifies a threat, Elisity can automatically adjust policies. When your vulnerability scanner finds a critical exposure, affected devices can be isolated until patched. This integration creates a self-healing security fabric that strengthens automatically.
Making CISA's Microsegmentation in Zero Trust Vision Achievable
The gap between security guidance and operational reality has plagued enterprises for too long. CISA's Microsegmentation in Zero Trust, Part One: Introduction and Planning document provides much-needed clarity on what modern network security should look like. But without the right implementation approach, even the best guidance remains theoretical.
Elisity bridges this gap by delivering enterprise-grade microsegmentation that's both sophisticated and simple to deploy. By leveraging existing infrastructure, automating complex tasks, and providing intuitive management tools, Elisity makes the vision outlined in CISA's microsegmentation guidance achievable for organizations of all sizes.
The evidence speaks through customer outcomes. When Main Line Health needed to protect 5 hospitals, health centers, and over 40 offices, traditional approaches would have required massive teams and years of effort. With Elisity, they achieved comprehensive microsegmentation aligned with CISA's Zero Trust principles with just a few people, implementing policies that now protect over 100,000 devices.
For organizations ready to move beyond planning to protection, the path is clear. CISA has provided the roadmap with Microsegmentation in Zero Trust, Part One: Introduction and Planning. Elisity provides the vehicle to get there quickly, safely, and cost-effectively.
Ready to implement CISA's Microsegmentation in Zero Trust, Part One: Introduction and Planning guidance in your organization? Download our microsegmentation solution brief to see how Elisity can transform your network security in weeks, not years. Or better yet, schedule a demonstration with our experts to see exactly how Elisity aligns with CISA's microsegmentation guidance in your environment. Join the growing number of enterprises that have discovered the secret to achieving Zero Trust at the speed of business.
Share this
- Enterprise Cybersecurity (59)
- Zero Trust (25)
- Microsegmentation (23)
- Enterprise Architecture Security (13)
- Lateral Movement (10)
- Elisity (8)
- Network Security (8)
- Ransomware (6)
- Identity (5)
- Cyber Resilience (4)
- Cybersecurity Healthcare (4)
- Elisity Release (4)
- Remote Access (4)
- ICS Security (3)
- Identity and Access Management (2)
- Industrial Cybersecurity (2)
- OT Security (2)
- S4x26 (2)
- AI Security (1)
- Agentic AI (1)
- Forrester (1)
- MITRE (1)
- February 2026 (12)
- January 2026 (4)
- December 2025 (4)
- November 2025 (3)
- October 2025 (5)
- September 2025 (4)
- August 2025 (5)
- July 2025 (5)
- June 2025 (5)
- May 2025 (4)
- April 2025 (5)
- March 2025 (6)
- February 2025 (3)
- January 2025 (5)
- December 2024 (4)
- November 2024 (5)
- October 2024 (7)
- September 2024 (5)
- August 2024 (3)
- July 2024 (4)
- June 2024 (2)
- April 2024 (3)
- March 2024 (2)
- February 2024 (1)
- January 2024 (3)
- December 2023 (1)
- November 2023 (1)
- October 2023 (2)
- September 2023 (3)
- June 2023 (1)
- May 2023 (3)
- April 2023 (1)
- March 2023 (6)
- February 2023 (4)
- January 2023 (3)
- December 2022 (8)
- November 2022 (3)
- October 2022 (1)
- July 2022 (1)
- May 2022 (1)
- February 2022 (1)
- November 2021 (1)
- August 2021 (1)
- May 2021 (2)
- April 2021 (2)
- March 2021 (3)
- February 2021 (1)
- November 2020 (2)
- October 2020 (1)
- September 2020 (1)
- August 2020 (3)




No Comments Yet
Let us know what you think