Solution Comparison
NAC Wasn’t Built For Speed, Evolving Threats, and Devices
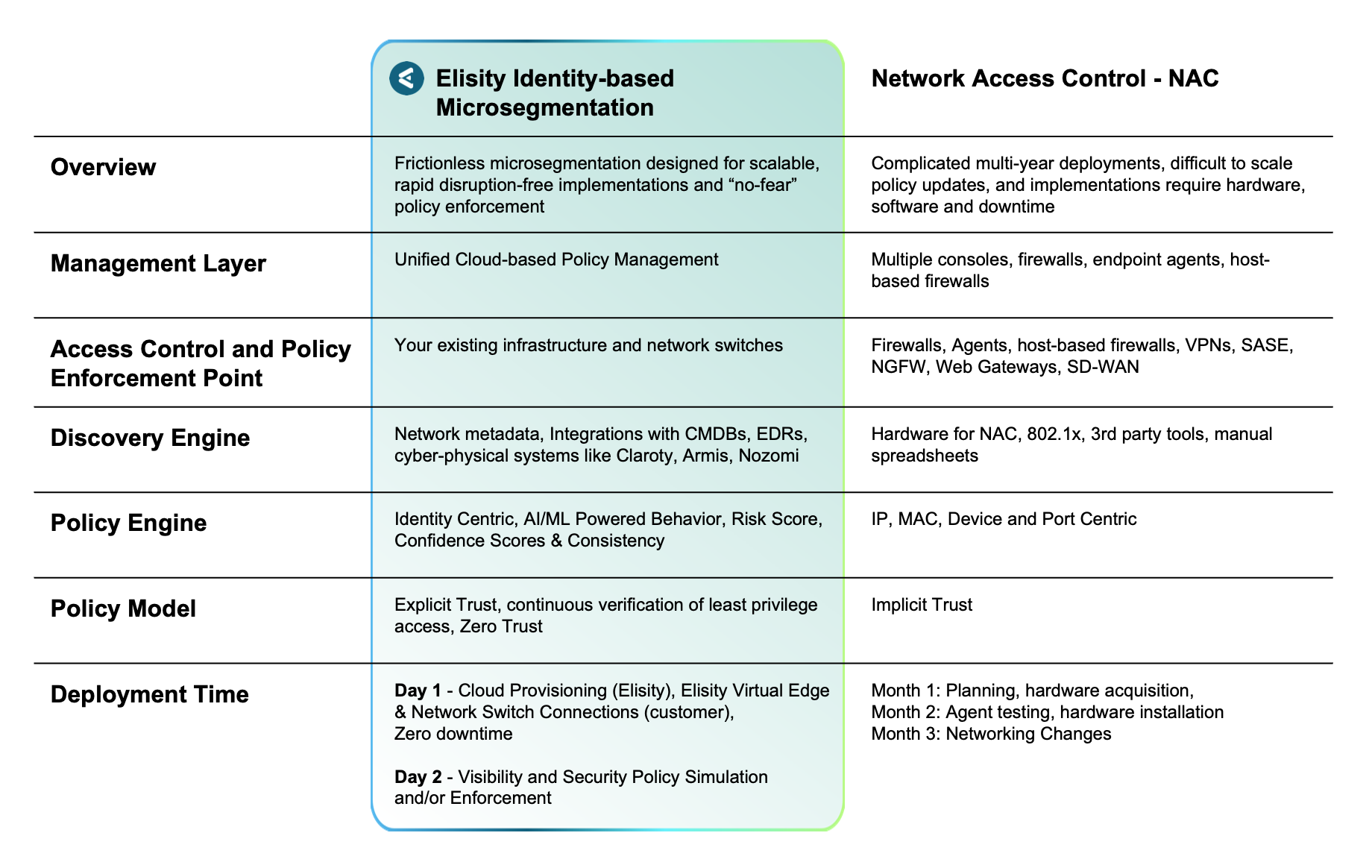
Network Access Control decides who gets on your network. Identity-based microsegmentation controls what happens next. While NAC projects stall in complexity, Elisity deploys in weeks using existing infrastructure—stopping lateral movement without the pain of 802.1X, VLANs, or endless ACLs.
Challenges
NAC promised control but delivered complexity. Years of planning. Specialized teams for 802.1X. VLAN sprawl. Firewall bottlenecks. Agent headaches. Multiple consoles. And still—threats move laterally. The problem isn't access control at the perimeter. It's what happens inside your network. Identity-based microsegmentation stops lateral movement and can be implemented in weeks using infrastructure you already own.
Network Segmentation Without Compromise
Challenge
Months-Long Deployment Cycles
Multi-month planning, hardware acquisition, 802.1X configuration, VLAN redesign, and agent rollouts. Requires specialized teams, extensive network changes and change control windows. Most projects extend beyond initial timelines with ongoing troubleshooting. Each site needs on-site resources, creating bottlenecks and delays across enterprise deployments.

Elisity Solution
Deploy In Weeks, Not Months
Deploys in weeks with zero downtime using your existing network infrastructure. Cloud-based Elisity Virtual Edge connects in minutes. First policies can be active or simulated in days. No hardware, no 802.1X, no VLANs, no re-IPing projects. Remote implementation across all sites eliminates travel costs. 75% faster than legacy approaches with automated discovery and classification.
Challenge
Console Sprawl Nightmare
Separate consoles for NAC, firewalls, endpoint agents, and SIEM. Policy changes require coordination across multiple teams and platforms. No unified view of network activity. Manual synchronization creates security gaps. Teams waste hours logging into different systems to troubleshoot issues and understand network behavior.

Elisity Solution
Single Cloud Delivered UX
Unified Elisity Cloud Control Center manages all policies, analytics, and compliance across every site. One console for discovery, segmentation, simulation, and enforcement. Real-time visibility into users, devices, and traffic flows. Elisity IdentityGraph™ correlates data from 25+ integrations. Push-button compliance reports eliminate manual audit prep.
Challenge
IoT and OT Blind Spots
Agent-based approaches fail with IoT, OT, medical devices, and legacy systems. Passive profiling via 802.1X or RADIUS leaves gaps. Many devices don't support supplicants. Manual MAC address lists become unmanageable at scale. Device fingerprinting degrades as new devices join, requiring constant manual updates.

Elisity Solution
Complete Device Coverage
Agentless discovery of every device—managed, unmanaged, IoT, OT. Native network metadata plus 50+ integrations with Cyber-Physical Systems like Claroty, Armis, CMDBs like ServiceNow, and EDRs like CrowdStrike and SentinelOne. 99% auto-classification accuracy, manual effort is eliminated. Policies persist regardless of device type. Elisity IdentityGraph™ enriches context from authoritative sources.
Challenge
Perimeter-Only Protection
NAC controls network entry but can't prevent east-west movement once devices authenticate. Attackers bypass perimeter controls and move laterally across flat networks. Macro-segmentation via VLANs creates overly broad trust zones. 70% of breaches involve lateral movement NAC wasn't designed to stop.

Elisity Solution
Zero Trust Everywhere
Identity-based policies enforce least privilege at every connection point across your network. Continuous verification prevents lateral movement. Dynamic segmentation adapts in real-time to risk and behavior changes. No implicit trust zones—only explicit authorization. Automated containment limits blast radius when incidents occur.
Challenge
Brittle IP-Based Policies
Policies tied to IP addresses, VLANs, and port assignments break when devices move across the network. Manual ACL updates required for every change. TCAM limitations restrict policy scale and granularity. No simulation—changes go live blindly. Network teams bottleneck security evolution. Policy drift creates exploitable gaps.

Elisity Solution
Static or Dynamic Identity Based Policies
Policies follow device identity, not location or IP address. AI-powered recommendations based on behavior and risk scores. Policy simulation validates changes before enforcement. No network changes required—updates happen automatically. Elisity IdentityGraph™ maintains context as devices roam. Continuous recommendations adapt to changes.
Challenge
Needs 14+ FTEs
Requires dedicated teams for Security Ops, Security Engineering, NAC platform management, and Network Engineering. Constant troubleshooting of authentication failures and policy conflicts. Manual updates for every change. Vendor-specific expertise needed. High turnover costs as specialists leave requiring months of training.

Elisity Solution
Potentially Just 2 FTEs
75% reduction in operational overhead compared to legacy approaches. Two engineers manage entire deployment across all sites and infrastructure. Automated classification and policy recommendations eliminate manual work. Vendor-neutral approach needs no specialized training. Cloud-delivered updates require no maintenance windows.
Stop East-West Attacks, Microsegment Your Networks
Network Asset Control FAQ
Want to know how Elisity discovers every device across your network — even the ones your current tools miss? Here are answers to common questions about asset visibility, classification, and what makes Elisity’s approach unique.
NAC (Network Access Control) controls who gets on your network by authenticating devices at the perimeter using 802.1X or RADIUS. Microsegmentation controls what devices can communicate with after they're on the network by enforcing identity-based policies at every connection point. While NAC provides perimeter security, microsegmentation prevents lateral movement—the attack vector used in 70% of successful breaches. Elisity's identity-based microsegmentation works alongside existing NAC solutions or replaces them entirely, deploying in 2 weeks versus 3-12 months for traditional NAC implementations.
Traditional NAC deployments typically require 3-12 months involving hardware procurement, 802.1X configuration, VLAN redesigns, and multi-team coordination. Elisity's microsegmentation deploys in 2 weeks. We can turn switches, WLCs, Firewalls into enforcement points. Day 1 focuses on cloud provisioning and Virtual Edge software deployment. Day 2 enables visibility and first security least privilage access security policies. Within 1 week, you can achieve full policy enforcement across all sites—a 75% reduction in deployment time compared to legacy NAC approaches.
NAC projects fail due to complexity, resource constraints, and scope creep. Enterprises struggle with 802.1X authentication issues, VLAN sprawl, ACL management at scale, and the need for 14+ FTEs across Security Ops, Network Engineering, and platform management teams. Integration challenges with heterogeneous infrastructure (mixing Cisco, Aruba, Juniper, Arista, Hirshmann) create deployment bottlenecks. Additionally, NAC only controls perimeter access—it doesn't prevent lateral movement once attackers authenticate, leaving organizations vulnerable despite the investment. 76% of enterprises using NAC report adoption has plateaued due to these operational challenges.
Yes, Elisity's microsegmentation complements existing NAC deployments. NAC handles authentication and initial network access, while Elisity enforces continuous identity-based policies that prevent lateral movement after devices authenticate. This layered approach maximizes your NAC investment while addressing its fundamental limitation—lack of east-west traffic control. Organizations can deploy Elisity alongside NAC solutions without replacing infrastructure, or gradually transition from NAC to Elisity's identity-based approach as a complete network access control alternative. The integration requires no changes to your NAC configuration.
Replace NAC when projects stall beyond 6 months, operational costs exceed 10+ FTEs, or lateral movement concerns outweigh perimeter control needs. Organizations should transition when facing NAC deployment complexity with 802.1X, VLAN limitations, or multi-vendor infrastructure incompatibility. If your network includes significant IoT/OT devices that can't support NAC agents or supplicants, microsegmentation provides better coverage. Consider replacement when pursuing Zero Trust architecture, as microsegmentation natively supports continuous verification versus NAC's point-in-time authentication model. Elisity can complement existing NAC initially, then replace it as your primary access control solution.
Traditional NAC total cost of ownership includes software licenses, hardware appliances, 14+ FTE operational staff, and 3-12 month deployment professional services. Enterprises typically spend $500K-$2M+ annually depending on scale. Elisity's microsegmentation reduces operational overhead by 75%, requiring only 2 FTEs for management, and deploys in weeks versus months—significantly lowering professional services costs. Elisity is cloud-delivered with no hardware requirements, eliminating capital expenditure on appliances. Organizations typically see ROI within 6-9 months through reduced staffing needs, faster deployment, and prevention of costly breach-related lateral movement (average breach cost: $4.45M).
Resources

Elisity 16.13: Enhanced Asset Intelligence and Granular Control Accelerate Enterprise Microsegmentation

Elisity Named a Cool Vendor in the Gartner® Cool Vendors™ in Cyber-Physical Systems Security 2025 Report: Transforming Critical Infrastructure Protection Through Identity-Centric Microsegmentation




