Forrester Wave™ Microsegmentation: The Golden Age of Zero Trust Network Security
Let's dig into the details about the report, microsegmenation, and Zero Trust strategies.
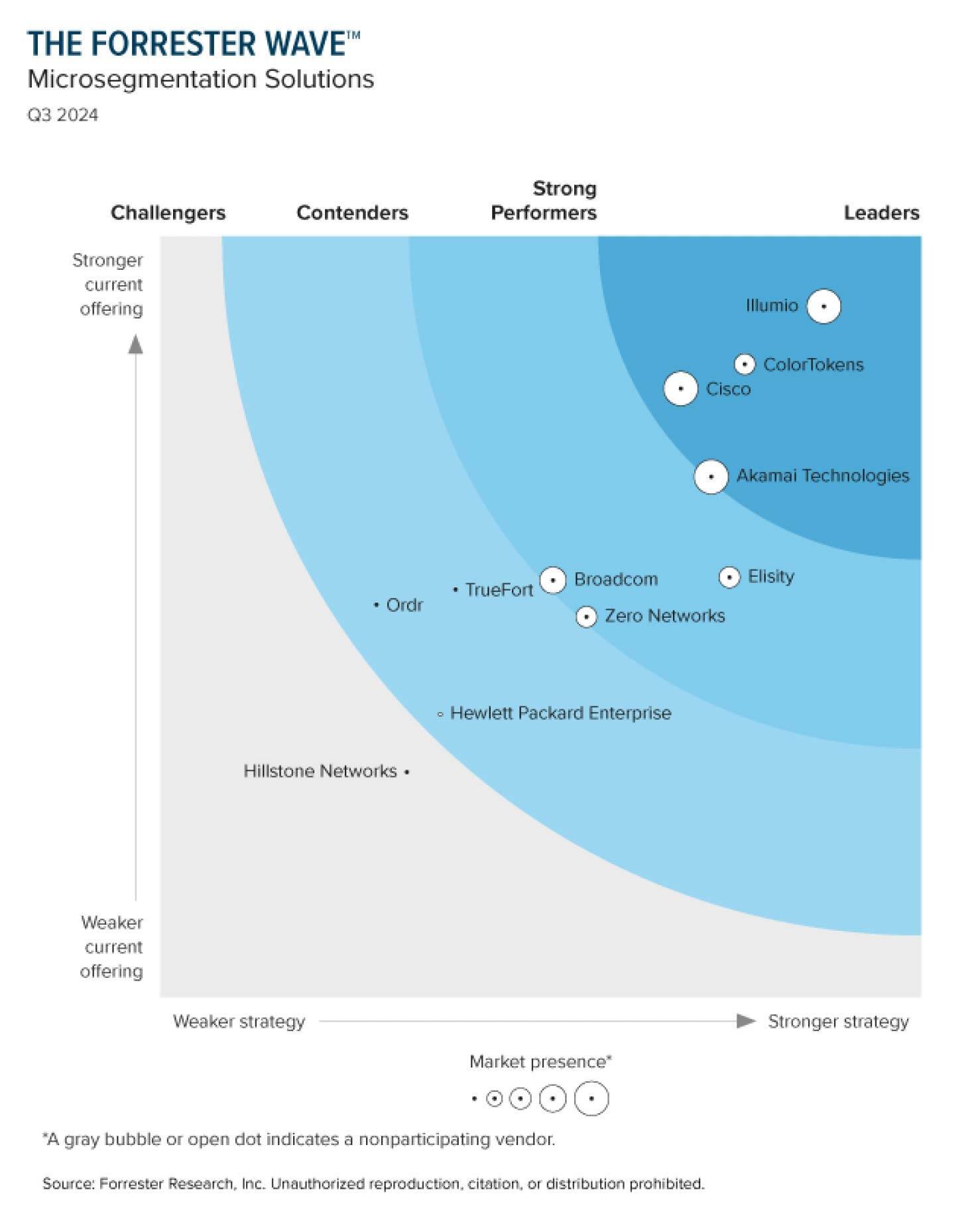
The latest Forrester Wave™ report on Microsegmentation Solutions is published. In today's rapidly evolving cybersecurity landscape, organizations are constantly seeking innovative ways to protect their digital assets from increasingly sophisticated threats. One approach that has gained significant traction in recent years is microsegmentation, a key component of the Zero Trust security model. As we delve into the world of microsegmentation, we'll explore its definition, history, and importance in modern cybersecurity strategies, with a particular focus on the insights provided by the latest Forrester Wave™ report on Microsegmentation Solutions. Some of the industries that are most rapidly adopting Zero Trust and Microsegmentation strategies include Healthcare IT and Manufacturing IT.
Before we dive into the evolution of Zero Trust and microsegmentation, it's crucial to have a solid grasp of what microsegmentation is and how it works.
If you're new to this concept or need a refresher, we recommend starting with our comprehensive guide: What is microsegmentation and how does it work?
This article covers: the fundamental principles of microsegmentation, how microsegmentation is implemented in practice, key benefits and challenges of microsegmentation and the best practices for successful implementation.
Understanding these basics will provide you with a strong foundation as we explore how microsegmentation has evolved and its role in modern Zero Trust architectures.
To learn how the new Forrester Wave™ report relates to manufacturing and industrial companies, read this blog.
To learn how the new Forrester Wave™ report relates to healthcare IT read this blog.
To learn how the new Forrester Wave™ report relates to Higher Ed and School Districts, read this blog.
To learn how the new Forrester Wave™ report relates to Water and Waste Water utilities, read this blog.
Understanding Network Segmentation and Microsegmentation
Before we dive into the intricacies of microsegmentation, it's essential to understand its foundational concept: network segmentation. Network segmentation is the practice of dividing a computer network into smaller subnetworks or segments to improve security, performance, and manageability. This approach has been used for decades to create boundaries within networks, limiting the potential spread of security breaches and improving overall network efficiency.
Microsegmentation takes this concept to the next level by implementing fine-grained security policies at the workload or application level. It allows organizations to create secure zones within their IT infrastructure and cloud environments, segmenting workloads from one another and securing them individually. This granular approach to security enables organizations to apply the principle of least privilege, ensuring that only authorized entities can access specific resources.
As noted by Louis Columbus, a LinkedIn Top Voice in Enterprise Software and Cybersecurity, microsegmentation has become synonymous with Zero Trust architecture. In his article on Forrester's take on the microsegmentation solutions landscape, Columbus highlights how microsegmentation has evolved to become a critical component of modern cybersecurity strategies.
It's worth noting that microsegmentation architectures are evolving faster than their Wikipedia descriptions might suggest. While traditional network segmentation still has its place, today's powerful systems, fast networks, and Zero Trust strategies have sparked increased interest in "going all the way" with microsegmentation, rather than relying solely on broader network segmentation techniques.
Forrester Wave™ Microsegmentation Solutions, Q3 2024 Download
The Evolution of Zero Trust and Microsegmentation
To fully appreciate the importance of microsegmentation, we need to understand its relationship with the Zero Trust security model. Zero Trust is a security concept based on the principle of "never trust, always verify." It assumes that no user, device, or network should be automatically trusted, regardless of whether they are inside or outside the organization's network perimeter. Many describe the difference as being between "explicit trust" vs. "implicit trust".
The Zero Trust model has gained significant traction in recent years, driven by the increasing complexity of IT environments, the rise of cloud computing, and the growing sophistication of cyber threats. As organizations move away from traditional perimeter-based security models, Zero Trust has emerged as a more effective approach to protecting modern, distributed networks. Some of the key industries that are rapidly adopting Zero Trust and microsegmentation include Healthcare IT and Manufacturing IT.
Microsegmentation plays a crucial role in implementing Zero Trust by providing the granular control and visibility needed to enforce security policies at a highly detailed level. As Carlos Rivera points out in his Forrester blog post, microsegmentation has become synonymous with Zero Trust, highlighting its importance in modern cybersecurity strategies.
The Five Pillars of Zero Trust
To fully understand how microsegmentation fits into the broader Zero Trust framework, it's helpful to consider the five pillars of Zero Trust:
- Identity: Verifying and securing all users, whether they're inside or outside the organization's network.
- Devices: Monitoring and securing all devices accessing the network, including IoT devices.
- Networks: Segmenting, isolating, and controlling the network to prevent lateral movement.
- Applications: Securing and monitoring all applications, including cloud-based and on-premises solutions.
- Data: Categorizing, encrypting, and limiting access to data based on its sensitivity.
Microsegmentation primarily addresses the network pillar of Zero Trust, but its effects ripple through the other pillars as well. By providing granular control over network traffic and access, microsegmentation supports the principles of least privilege and need-to-know access that are fundamental to Zero Trust.
The Benefits of Microsegmentation
Implementing microsegmentation offers several key advantages for organizations:
- Improved Security Posture: By creating smaller, more secure zones within the network, microsegmentation significantly reduces the attack surface and limits the potential spread of breaches.
- Enhanced Visibility: Microsegmentation provides detailed insights into network traffic patterns, making it easier to detect and respond to anomalies.
- Compliance Support: Many regulatory frameworks require strict access controls and data protection measures. Microsegmentation helps organizations meet these requirements by providing granular control over data access.
- Flexibility and Scalability: Microsegmentation can be applied consistently across on-premises, cloud, and hybrid environments, making it ideal for modern, distributed IT infrastructures.
- Reduced Blast Radius: In the event of a security breach, microsegmentation limits the attacker's ability to move laterally within the network, containing the damage to a smaller area.
Implementing Microsegmentation: Top Methods and Approaches
Organizations can implement microsegmentation using various methods and technologies. Some of the top approaches include:
- Software-Defined Networking (SDN): Using SDN to create and manage virtual network segments, allowing for dynamic and flexible microsegmentation. The centralization of SDN networks at the controller level creates a big vulnerability surface that is a target for security threats.
- Host-Based Firewalls: Implementing firewalls at the host level to control traffic between individual workloads. These firewalls are difficult to implement and manage, and create potential performance bottlenecks with higher resource consumption and inconsistent policy enforcement.
- Network Virtualization: Leveraging network virtualization platforms to create isolated network segments for different applications or workloads. Similar to Host-Based Firewalls, Network Virtualization powered microsegmentation creates challenges with complexity, management, performance, scalability, downtime, and security gaps due to misconfiguration and reliance on virtualization platforms.
- Identity-Based Microsegmentation: Incorporating user and application identity into segmentation policies for more granular control. Perhaps the most granular method of achieving microsegmentation, this method provides better visibility into network traffic for users, workloads, and devices, facilitates rapid policy changes and automated response to risk changes, and prevents unauthorized access to sensitive resources.
Challenges in Microsegmentation Implementation
While the benefits of microsegmentation are clear, organizations often face challenges when implementing these solutions. Some of the top challenges include:
- Complexity: Implementing agents, VLANs, and ACLs and creating and managing policies across diverse environments can be complex and time-consuming.
- Legacy and Proprietary Hardware/Software Systems: Integrating microsegmentation with legacy systems and applications can be challenging.
- Policy Management: Maintaining and updating a large number of granular policies can be overwhelming, particularly with host-based firewalls, whereas a modern and automated, AI-assisted platform and UX can greatly simplify policy management.
- Performance Concerns: Complexity, misconfiguration, and choke points are signs of legacy architectures and can cause microsegmentation to potentially impact network performance.
- Skill Gap: Many organizations lack the in-house expertise needed to effectively design and implement legacy and complex host and agent-based microsegmentation strategies.
The Forrester Wave™: A Methodology for Evaluating Microsegmentation Solutions
The Forrester Wave™ reports are widely respected in the technology industry for their comprehensive and objective evaluations of various software solutions. The methodology used by Forrester to create these reports is rigorous and transparent, ensuring that the results provide valuable insights for organizations considering different technologies.
For the Forrester Wave™ Microsegmentation Solutions report, the process typically includes:
- Market Research: Forrester analysts conduct extensive research to identify the most significant vendors in the microsegmentation space.
- Evaluation Criteria: A set of evaluation criteria is developed based on customer needs and market trends.
- Vendor Surveys: Participating vendors complete detailed questionnaires about their products and services.
- Product Demos: Vendors provide demonstrations of their solutions to Forrester analysts.
- Customer References: Forrester speaks with customers of each vendor to gather real-world feedback.
- Analysis and Scoring: Based on all the gathered data, Forrester analysts score each vendor across multiple criteria.
- Report Creation: The final report is created, including detailed vendor evaluations and a visual representation of vendor positions in the market.
The Golden Age of Microsegmentation
According to the latest Forrester Wave™ Microsegmentation Solutions, Q3 2024 report, we are currently living in the "Golden Age of Microsegmentation." This assessment is based on several key observations:
- Rapid Evolution: Microsegmentation solutions have evolved significantly since the last evaluation in 2022, with capabilities expanding beyond traditional data center use cases.
- Broader Application: Leading solutions now offer unified approaches for data centers, microservices architectures, and public cloud environments.
- Immediate Value: Modern microsegmentation solutions can deliver immediate value by quickly tightening security postures, rather than requiring lengthy implementation processes.
- Identity Integration: Advanced solutions now incorporate identity-based policies, enabling more granular control and even auto-quarantine capabilities.
- Reduced Friction: New approaches to microsegmentation are reducing the friction associated with implementation, making it more accessible to a broader range of organizations.
The Future of Zero Trust Microsegmentation
Looking ahead, Forrester anticipates several trends that will shape the future of Zero Trust microsegmentation:
- Cloud-Native Integration: Deeper integration with cloud-native technologies and architectures will become increasingly important.
- AI and Machine Learning: Advanced analytics and machine learning will play a larger role in policy creation and threat detection.
- IoT and Edge Computing: Microsegmentation solutions will evolve to better address the unique challenges of IoT and edge computing environments.
- Automation and Orchestration: Increased automation in policy management and orchestration across diverse environments will be crucial.
Just a few months ago the NSA published a guide to Advancing Zero Trust with microsegmenation. Read more about it here.
The Value of Forrester Wave™ Reports in Cybersecurity
Forrester Wave reports are widely read and respected in the cybersecurity community, including:
- CISOs and Security Leaders: Who use these reports to inform their technology selection processes and strategic planning.
- IT Decision Makers: Who rely on the objective evaluations to shortlist and compare different solutions.
- Vendors: Who use the reports to understand their market position and areas for improvement.
- Analysts and Consultants: Who leverage the insights to advise their clients on technology choices.
The value of Forrester Wave reports for enterprises in the cybersecurity space is multifaceted:
- Objective Comparisons: They provide an independent, objective comparison of different solutions in the market.
- Time and Resource Savings: The comprehensive evaluations save organizations time and resources in their technology selection processes.
- Risk Mitigation: By highlighting strengths and weaknesses of different solutions, these reports help organizations mitigate the risks associated with technology investments.
- Market Insights: They offer valuable insights into market trends and the direction of technology evolution.
- Vendor Accountability: The reports hold vendors accountable for their claims and capabilities, benefiting the entire industry.
Conclusion: Embracing the Future of Network Security
As we navigate the complexities of modern cybersecurity, microsegmentation stands out as a critical component of effective Zero Trust strategies. The insights provided by the Forrester Wave™ report on Microsegmentation Solutions underscore the rapid evolution and growing importance of this technology in securing today's diverse and distributed IT environments.
Organizations looking to enhance their security posture, improve compliance, and effectively implement Zero Trust principles should carefully consider the role of microsegmentation in their cybersecurity strategy. By leveraging the latest advancements in microsegmentation technology, businesses can better protect their critical assets, reduce their attack surface, and stay ahead of evolving threats.
As we continue to witness the "Golden Age of Microsegmentation," it's clear that this technology will play an increasingly vital role in shaping the future of network security. By staying informed about the latest developments and leveraging insights from respected sources like the Forrester Wave™ reports, organizations can make informed decisions that will strengthen their cybersecurity posture for years to come.
To gain a deeper understanding of the current microsegmentation landscape and to inform your organization's cybersecurity strategy, we encourage you to download the latest Forrester Wave™ Microsegmentation Solutions, Q3 2024 report.
Download the Forrester Wave™ Microsegmentation Solutions Q3, 2024 report
By staying informed and embracing innovative solutions like microsegmentation, organizations can build resilient, secure networks that are prepared to face the challenges of today's dynamic threat landscape.
The Forrester Wave™ Microsegmentation Solutions, Q3 2024 Download
The Forrester Wave™ is copyrighted by Forrester Research, Inc. Forrester and Forrester Wave are trademarks of Forrester Research, Inc. The Forrester Wave is a graphical representation of Forrester's call on a market and is plotted using a detailed spreadsheet with exposed scores, weightings, and comments. Forrester does not endorse any vendor, product, or service depicted in the Forrester Wave. Information is based on best available resources. Opinions reflect judgment at the time and are subject to change.
Read and Follow Our Blog for More Insights

CISA Microsegmentation in Zero Trust, Part One: Introduction and Planning - How Elisity Makes It Actionable
Zero Trust Assessment for Pharmaceutical and BioTech Companies: A Practical Implementation Guide




