Microsegment Everything In Weeks, Not Years
Close Security Gaps and Regain Control of Your Security Posture
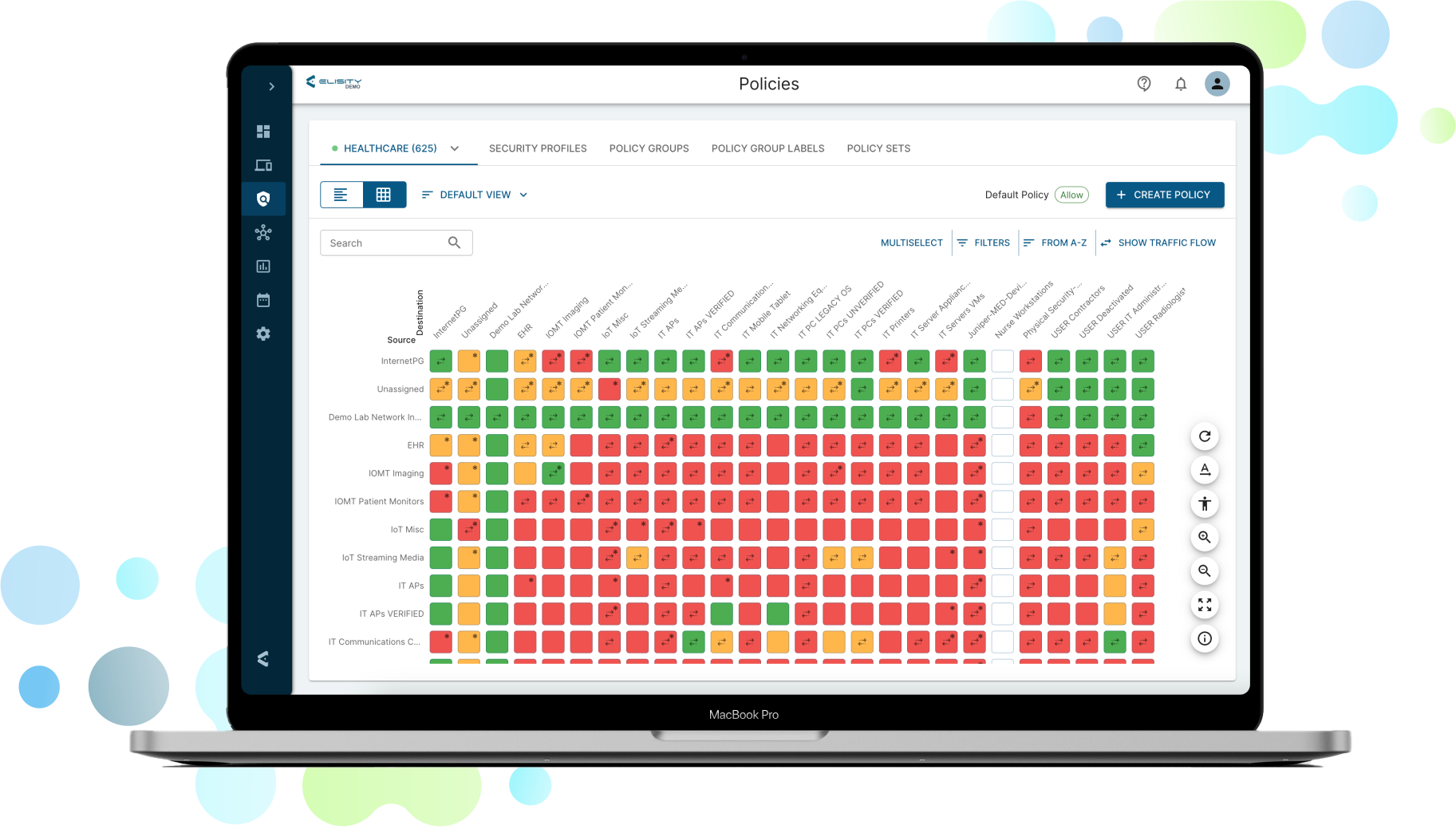
Elisity's cloud-delivered policy management platform discovers, correlates, and segments every device on your network, providing unparalleled visibility and control.
DISCOVERY
Discover and visualize every device on your networks:
- Discover 100% of devices on your network, including IoT, OT, IoMT, and shadow IT
- Visualize connections and dependencies with our intuitive graph interface
- Integrate with your existing infrastructure in under 4 hours
- Ingest metadata from your tech stack for 10x deeper insights
Challenges addressed: Eliminates network blind spots and provides a single source of truth for all connected devices.
CONTROL
Apply security policies with confidence:
- Utilize our "no-fear" policy creation engine with built-in simulation capabilities
- Create, simulate, and apply dynamic security policies in minutes, not days
- Automate least privilege access for users, workloads, and devices, reducing over-privileged accounts by up to 90%
- Protect against east-west attacks effortlessly, potentially preventing lateral movement risk by up to 85%
Challenges addressed: Overcomes the complexity and time-consuming nature of traditional policy creation and management.
MANAGE
Implement and manage segmentation with ease:
- Deploy at every location in hours, not months - typically 3-4 hours per site
- No additional firewalls, VLANs, or ACLs are required, reducing network complexity and firewall licenses by up to 65%
- Manage policies through our intuitive cloud interface, with a typical learning curve of just 2-3 days
- Adapt to network changes automatically, with realtime policy updates
Challenges addressed: Solves the ongoing struggle of maintaining an effective and current security posture in dynamic network environments.
“We deployed it at two of our sites in less than an hour, and by the next day, we were confidently implementing policies. This unprecedented speed and effectiveness soon made Elisity an indispensable part of our network security strategy across our manufacturing sites, protecting thousands of managed IT assets as well as our growing number of unmanaged IoT and OT assets”

Max Everett
CISO at Shaw Industries
Prevent East-West Attacks, Microsegment Your Networks
Learn why and how large enterprises are reducing risks and accelerating their Zero Trust maturity with Elisity.
Elisity Architecture Overview
Elisity transforms your existing switching infrastructure into policy enforcement nodes through our innovative technology called Elisity Virtual Edge. Elisity Virtual Edge translates identity and policy data from the Elisity Cloud Control Center into policy enforcement mechanisms native to the onboarded switches, called Virtual Edge Nodes (VENs). This approach allows rapid onboarding of existing infrastructure into the Elisity fabric, with large numbers of VENs controlled by a single Elisity Virtual Edge.
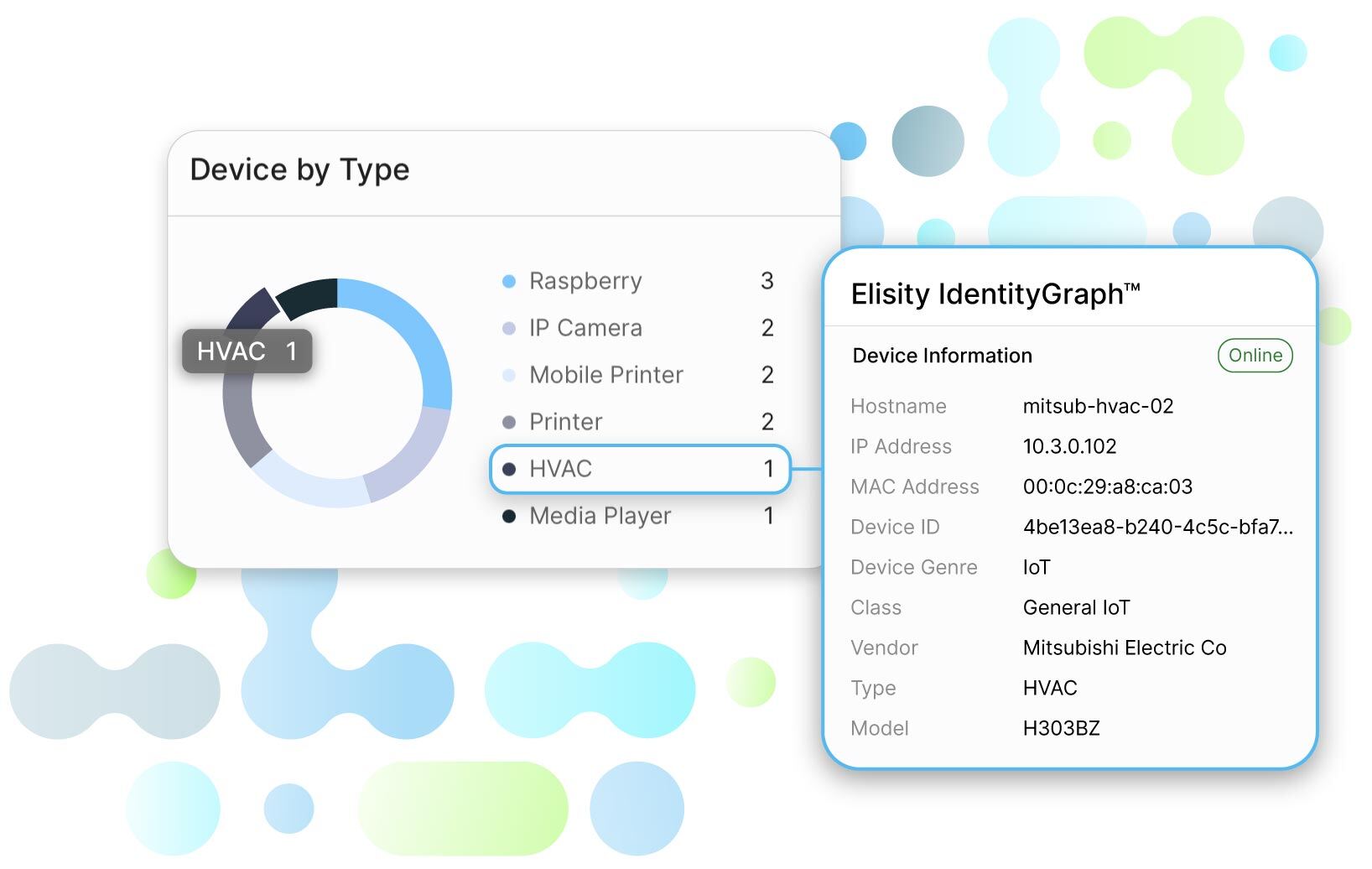
Elisity IdentityGraph™
Creates a real-time, correlated visibility of user, workflow, and device metadata and relationships across the network, enabling teams with the confidence needed to create policies.
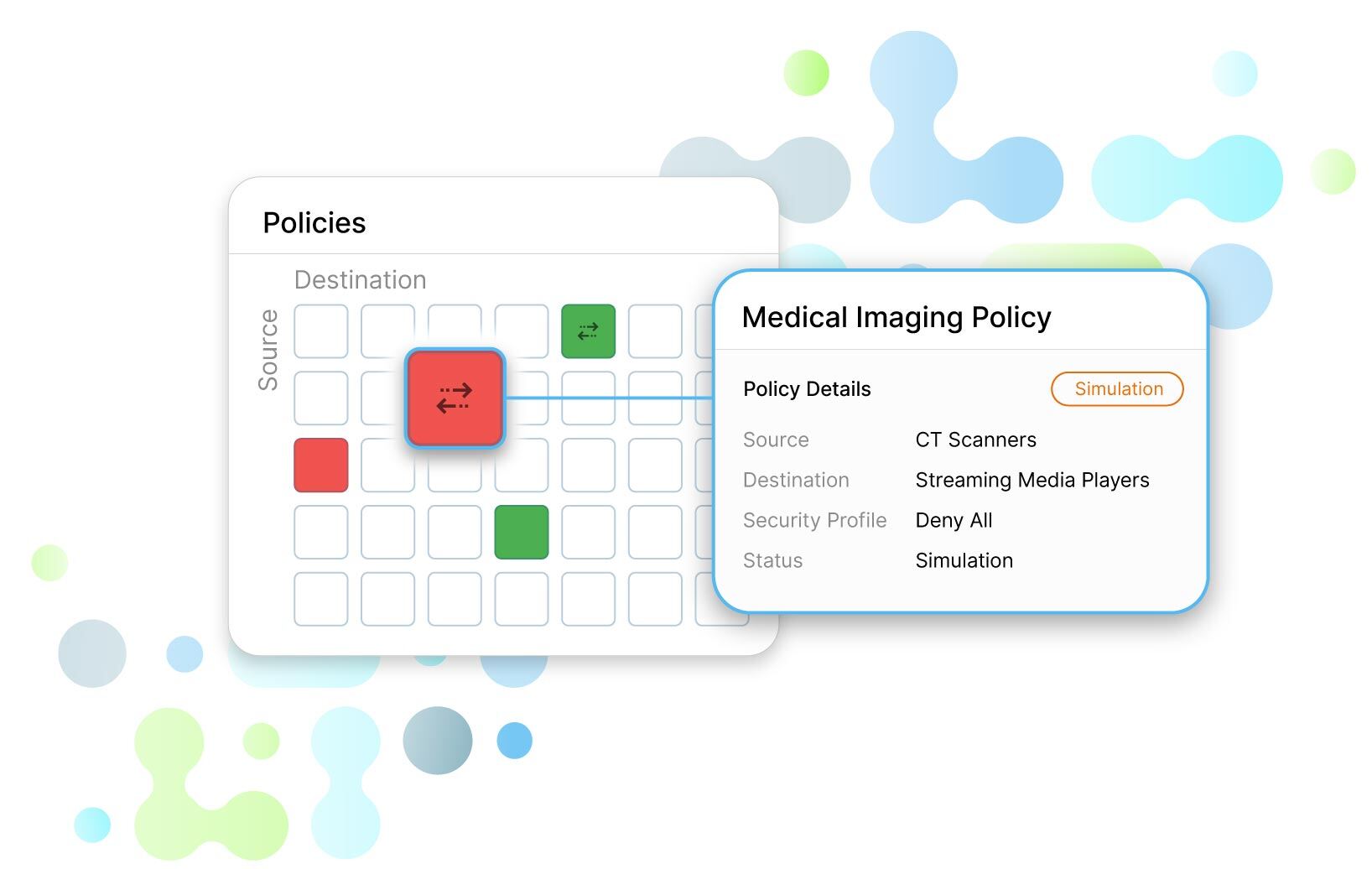
Dynamic Policy Engine
Enables the creation and enforcement of dynamic, context-aware policies based on the rich identity information provided by IdentityGraph. Ensures granular control over network access.
Elisity Virtual Edge
Software that gleans asset identity and enforces identity-based policies at the network edge. Flexible deployment options, including switch-hosted or hypervisor-hosted.

Your Cisco, Juniper or Arista Switches
No agents. No hardware. No ACLS, VLANs or Re-IPing Projects, Elisity utilizes your high-performance network infrastructure to enforce policies that are managed in the Elisity SaaS platform.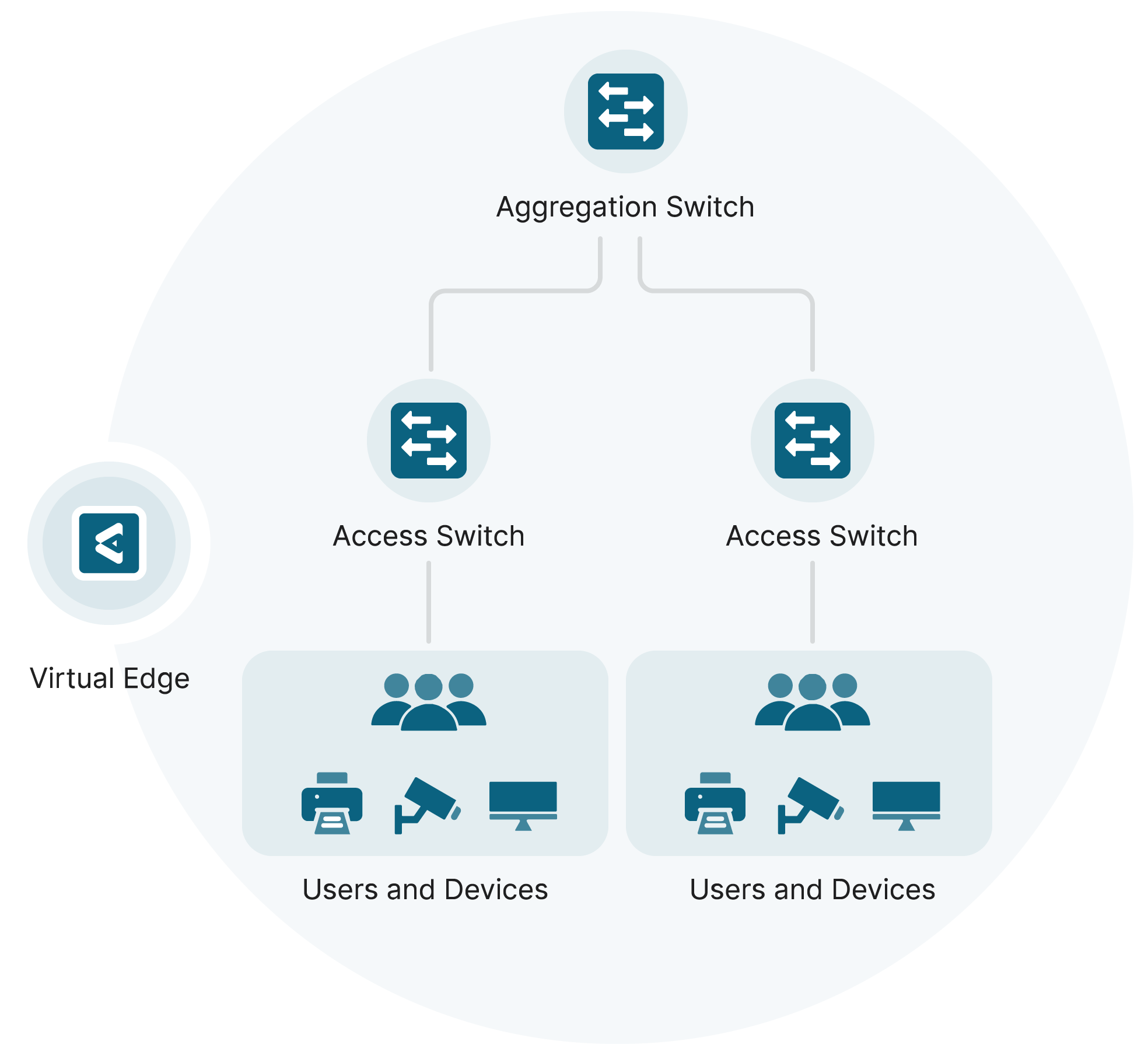
Your Networks, Locations, Switch Infrastructure and Users, Applications and Devices
Integrations
Elisity’s platform, powered by AI, is capable of discovering, classifying, and monitoring users, workloads, and devices. It ingests device metadata from various sources in your stack such as Active Directory, CrowdStrike, Claroty, Armis, and more. It then correlates that data, enabling your team with the context needed for policy automation. Additionally, our platform integrates with popular access switches from Cisco, Arista, and Juniper.











“Elisity’s identity-based microsegmentation brings tremendous capabilities to our security stack as a critical control point for containing ransomware, blocking malicious lateral network traffic and minimizing incident blast radius, and Elisity features prominently for our present and forward-looking security posture, allowing us to easily adjust to new regulatory as well as threat landscape developments.”

Aaron Weismann
CISO at Main Line Health
Lateral Movement Prevention
Contain Threats and Limit the Blast Radius
Microsegmentation of every device, everywhere on your network, is the best defense against lateral (east-west) movement of cyber attackers. Ransomware and active infiltrators utilize reconnaissance, credentials, and access to move closer to their targets. With Zero Trust explicit access policies for every user, workload, and device on your network, attackers will be blocked and contained.
Continuous Compliance
Automate Enforcement and Audit Reports
Elisity's reporting and audit logging streamline compliance audits, making them faster and easier while boosting your team's confidence. Ensure alignment with and adherence to NIST, PCI, HIPAA, 405 (d), IEC 62443, and other frameworks and regulations. Continuous discovery, correlation, and automated policy creation guarantee proactive protection against cyber threats for every device on your network.
Zero Trust Maturity
Accelerate Your Least Privilege Access Strategy
Elisity simplifies the process of applying least privilege access for your users, workloads, and devices, thereby enhancing your organization's protection against east-west attacks. Additionally, Elisity's robust discovery and correlation capabilities ensure that automated policies can be applied to every device, everywhere on your networks. And, Elistiy’s Dynamic Policy Engine enables policies to persist for every device, no matter where or when it appears on the network. Policy groups can be automatically applied based on policy classification details. Ultimately, this means that the chaos associated with unmanaged devices will be eliminated.
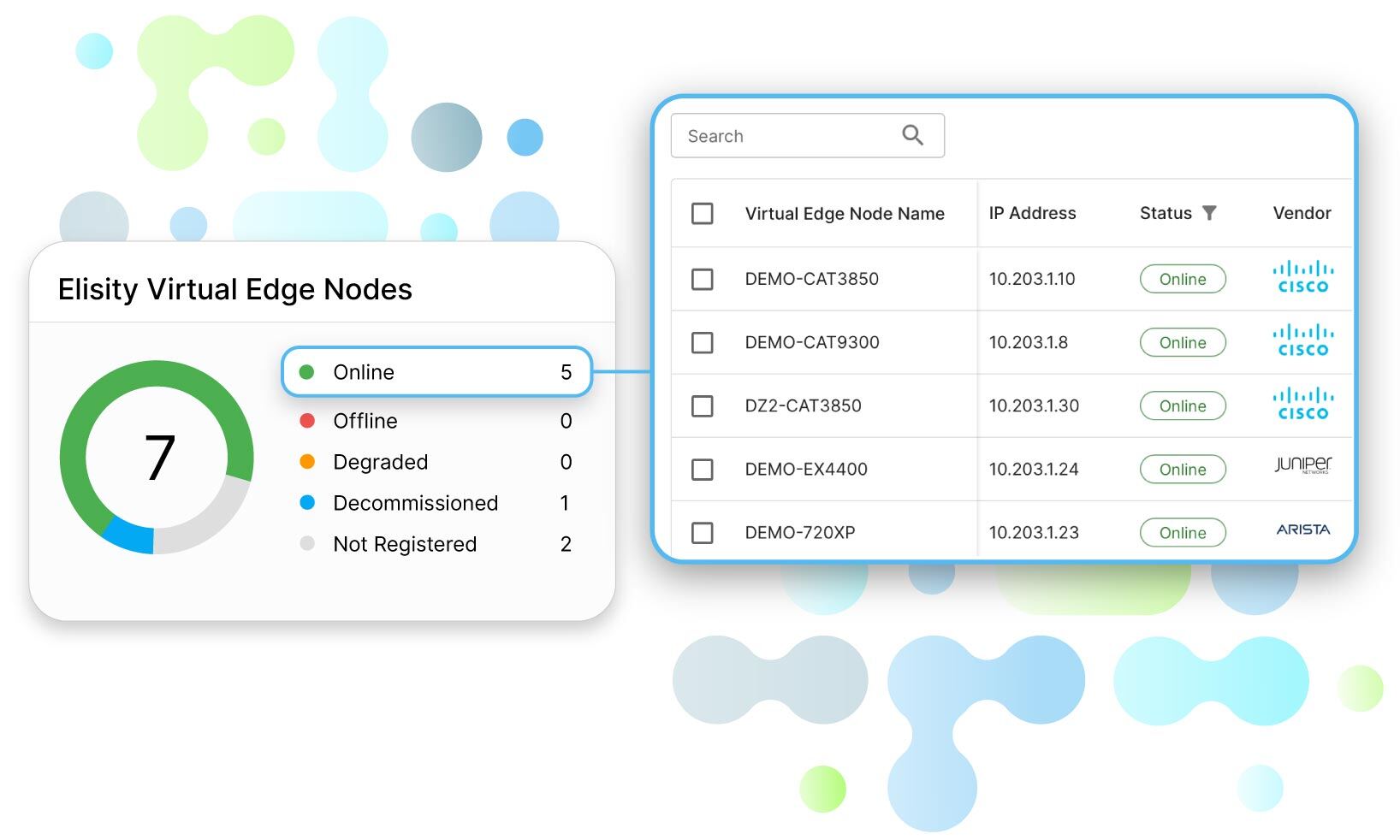
MANAGE
Implement and manage segmentation with ease:
- Deploy at every location in hours, not months - typically 3-4 hours per site
- No additional firewalls, VLANs, or ACLs are required, reducing network complexity and firewall licenses by up to 65%
- Manage policies through our intuitive cloud interface, with a typical learning curve of just 2-3 days
- Adapt to network changes automatically, with real-time policy updates
Challenges addressed: Solves the ongoing struggle of maintaining an effective and current security posture in dynamic network environments.
Industrial Networks
Flexible security for large-scale industrial operations.
Healthcare Facilities and Devices
From clinical locations to IoMT, safeguard patient networks.
Enterprise Networks
Proactively protect IT and IoT assets across networks
Secure Your Network Now
Don’t let threats take you by surprise. Reclaim control of your network's security posture with Elisity. Unlock enhanced threat detection and policy management capabilities to achieve cybersecurity objectives confidently.
