Microsegment Everything in Weeks, Not Years
Network Segmentation’s Leap Forward;
Microsegmentaiton in Weeks, Not Years.

Customer Spotlight
“We made more progress in 2 days with Elisity than we did in 2 years with our previous solution.”
Director of IT Security,
Andelyn Bio
The Numbers
Elisity secured and segmented Andelyn Bio’s network without re-IPing or new hardware. It provided enhanced visibility across Cisco, Arista, Juniper, and Palo Alto Networks.
2,000+
Policies enforced
10,000+
Devices protected
2
Days to deploy
4
Hours to first policy
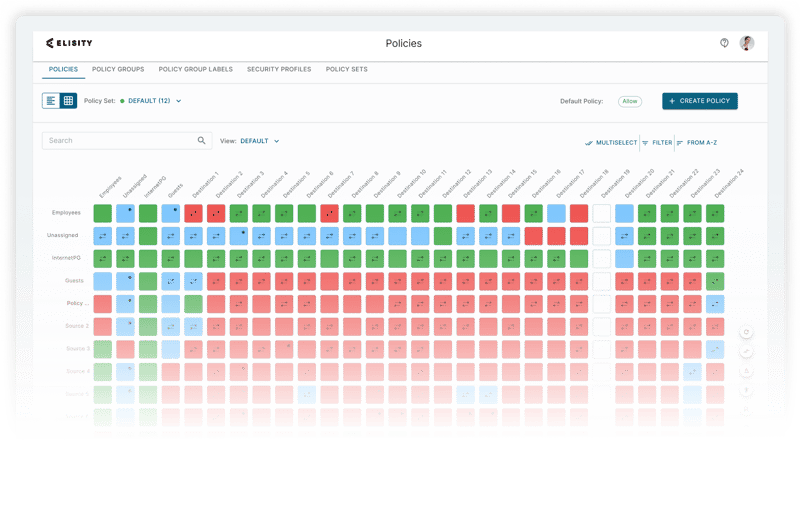
Network Segmentation Redefined: Elisity's Streamlined Approach
-
Discover
Discover and visualize every device on your networks
-
- Discover 100% of devices on your network, including IoT, OT, IoMT, and shadow IT
- Visualize connections and dependencies with our intuitive graph interface
- Integrate with your existing infrastructure in under 4 hours
- Ingest metadata from your tech stack for 10x deeper insights
- Discover 100% of devices on your network, including IoT, OT, IoMT, and shadow IT
Challenges addressed:
Eliminates network blind spots and provides a single source of truth for all connected devices. -
-
Control
Apply security policies with confidence
- Utilize our "no-fear" policy creation engine with built-in simulation capabilities
- Create, simulate, and apply dynamic security policies in minutes, not days
- Automate least privilege access for users, workloads, and devices, reducing over-privileged accounts by up to 90%
- Protect against east-west attacks effortlessly, potentially preventing lateral movement risk by up to 85%
Challenges addressed:
Overcomes the complexity and time-consuming nature of traditional policy creation and management. - Utilize our "no-fear" policy creation engine with built-in simulation capabilities
-
Manage
Implement and manage segmentation with ease
- Deploy at every location in hours, not months - typically 3-4 hours per site
- No additional firewalls, VLANs, or ACLs are required, reducing network complexity and firewall licenses by up to 65%
- Manage policies through our intuitive cloud interface, with a typical learning curve of just 2-3 days
- Adapt to network changes automatically, with realtime policy updates
Challenges addressed:
Solves the ongoing struggle of maintaining an effective and current security posture in dynamic network environments. - Deploy at every location in hours, not months - typically 3-4 hours per site


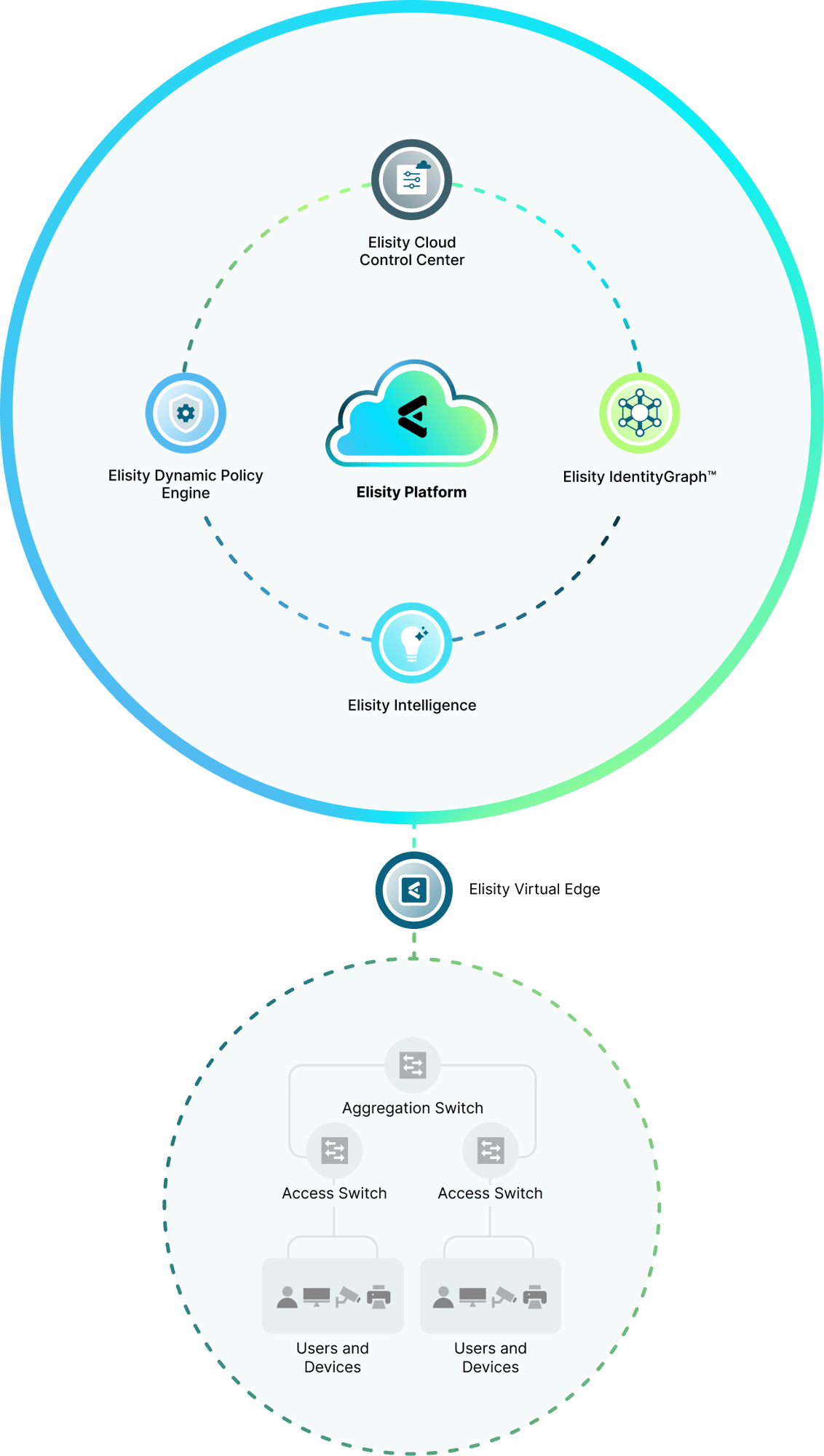
Elisity Identity-based Microsegementation Platform
Elisity transforms your existing switching infrastructure into policy enforcement nodes through our innovative technology called Elisity Virtual Edge. Elisity Virtual Edge translates identity and policy data from the Elisity Cloud Control Center into policy enforcement mechanisms native to the onboarded switches, called Virtual Edge Nodes (VENs). This approach allows rapid onboarding of existing infrastructure into the Elisity fabric, with large numbers of VENs controlled by a single Elisity Virtual Edge.
Elisity Cloud Control Center
An intuitive admin portal for configuring, monitoring, and managing the scale of network security policies. Provides centralized visibility and management of installed Elisity Virtual Edge deployments.
Elisity IdentityGraph
Creates a real-time, correlated visibility of users, workloads, & devices across your network. Automatically discovers and enriches identity data through multiple sources, enabling confident policy creation and enforcement.
Elisity Dynamic Policy Engine
Creates and enforces granular, context-aware dynamic and static security policies based on identity data and real-time risks. Works seamlessly with Elisity IdentityGraph to stop lateral movement threats and prevent unauthorized access.
Elisity Intelligence
Analyzes network patterns and metadata to identify vulnerabilities and threats. Provides automated risk scoring, policy recommendations, and continuous monitoring to prevent lateral movement and protect critical assets.
Elisity Virtual Edge
Lightweight container software that runs on existing switches or virtual environments. It synchronizes policies to your existing infrastructure enabling actionable controls and enforcement without requiring additional hardware.
Any Data Plane
No agents. No hardware. No ACLs, VLANs, or re-IPing projects. Elisity utilizes your high-performance network infrastructure including Cisco, Arista, and Juniper switches, as well as Palo Alto Networks firewalls, to enforce policies that are managed in the Elisity platform.
Elisity Platform Integrations
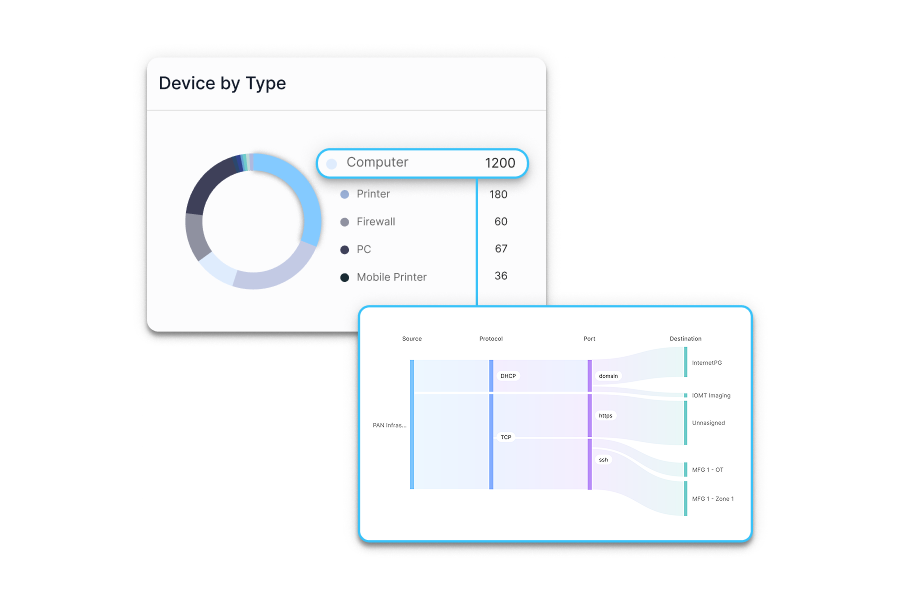
Elisity enforces least privilge access policies with your Cisco, Juniper or Arista switches. No agents. No hardware, ACLS, additional VLANs or Re-IPing projects required. In addition to Elisity’s powerful platform, Elisity gains deeper insights to your users, worloads, and devices by intergating with your stack via APIs. It aggregates user, workload and device data from all available sources and integrations, becoming a valuable dataset for flexible dynamic policies.
Discovery & Enrichment




Identity Enrichment
Your Policy Enforcement Infrastructure
CMDB & Workflow
Discover Elisity’s Deep Domain Expertise Across Industries
Get enterprise-wide protection and simplified management—deployed in weeks using your existing infrastructure. We can help find the right solution for your business, no matter the industry.

Manufacturing & Industrial Organizations
Strengthen your converged IT and OT environments and meet IEC 62443 requirements.

Commercial Enterprise
Meet compliance requirements and Zero Trust goals without painful agents and slow rollouts.

Healthcare Institutions
From clinical locations to IoMT, protect all users, workloads and devices and patient networks.
A Clear Comparison: The Elisity Microsegmentation Advantage

Explore Elisity’s Interactive Demo: See How It Works
Experience how Elisity discovers 99% of all users, workloads, and devices in one day, without agents or network changes. See firsthand how you can create, simulate, and automate least privilege access policies that prevent lateral movement while simplifying audit compliance in just weeks.
Launch Tour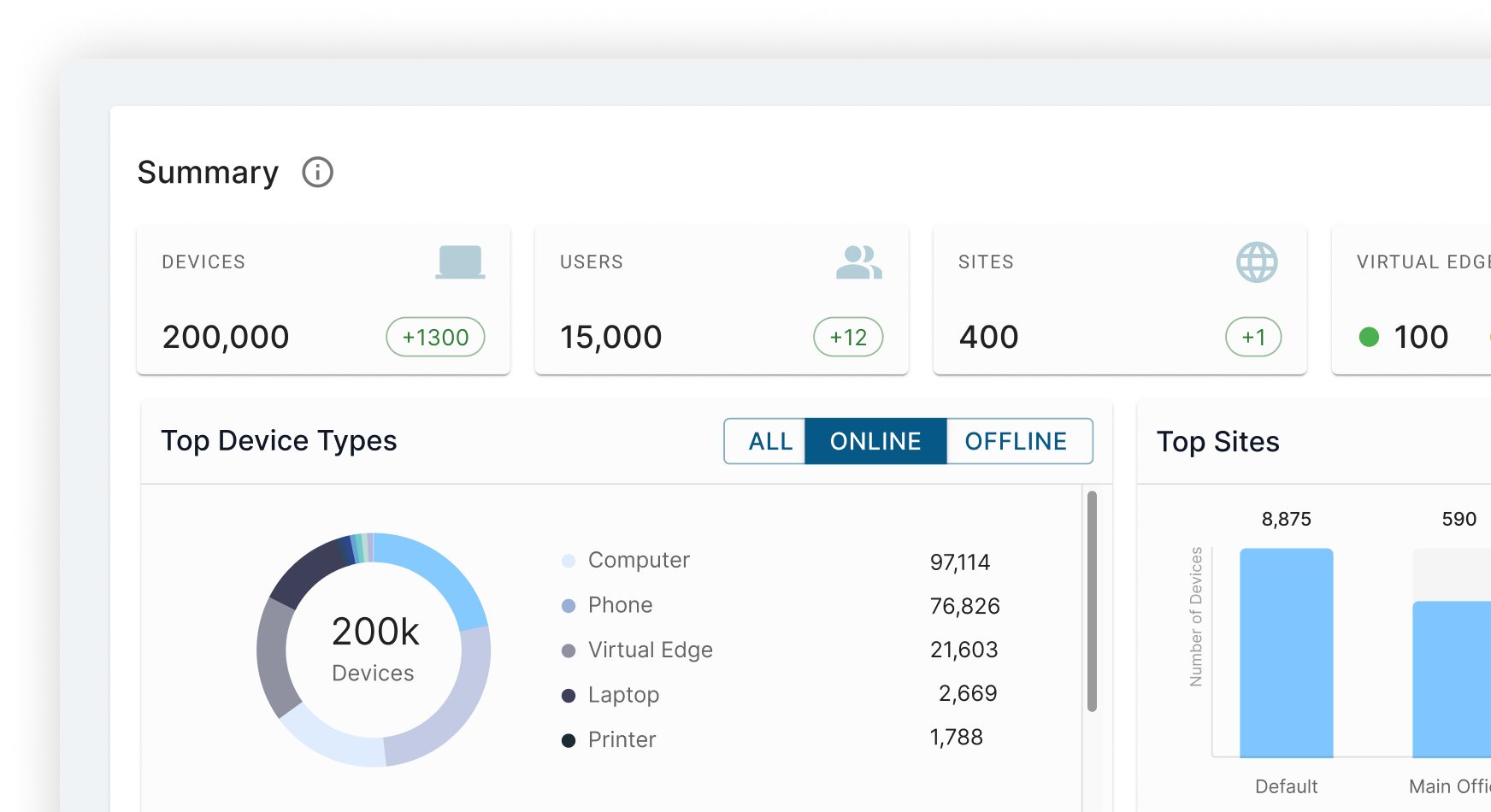
Proven Solutions for Your Most Critical Security Challenges
Our solutions span a vast range of different sectors. We can help you find the right solution for your business, no matter the industry.
-
Lateral Movement Prevention
-
Continuous Compliance
-
Content Management
-
Contain Threats and Limit the Blast Radius
Microsegmentation of every device, everywhere on your network, is the best defense against lateral (east-west) movement of cyber attackers. Ransomware and active infiltrators utilize reconnaissance, credentials, and access to move closer to their targets. With Zero Trust explicit access policies for every user, workload, and device on your network, attackers will be blocked and contained.
-

Automate Enforcement and Audit Reports
Elisity's reporting and audit logging streamline compliance audits, making them faster and easier while boosting your team's confidence. Ensure alignment with and adherence to NIST, PCI, HIPAA, 405 (d), IEC 62443, and other frameworks and regulations. Continuous discovery, correlation, and automated policy creation guarantee proactive protection against cyber threats for every device on your network.
-
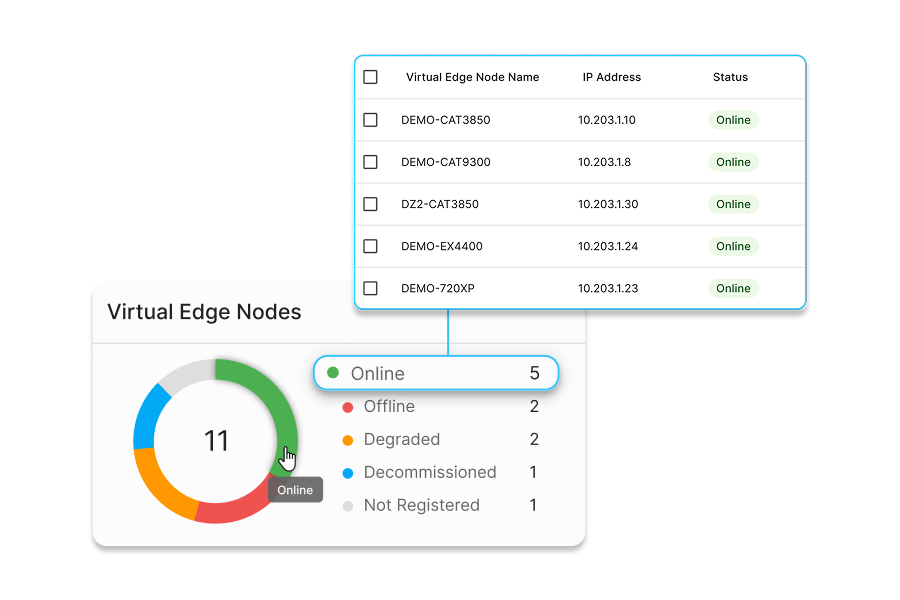
Accelerate Your Least Privilege Access Strategy
Elisity simplifies the process of applying least privilege access for your users, workloads, and devices, thereby enhancing your organization's protection against east-west attacks. Additionally, Elisity's robust discovery and correlation capabilities ensure that automated policies can be applied to every device, everywhere on your networks. And, Elistiy’s Dynamic Policy Engine enables policies to persist for every device, no matter where or when it appears on the network. Policy groups can be automatically applied based on policy classification details. Ultimately, this means that the chaos associated with unmanaged devices will be eliminated.
-

Contain Threats and Limit the Blast Radius
Microsegmentation of every device, everywhere on your network, is the best defense against lateral (east-west) movement of cyber attackers. Ransomware and active infiltrators utilize reconnaissance, credentials, and access to move closer to their targets. With Zero Trust explicit access policies for every user, workload, and device on your network, attackers will be blocked and contained.
-

Automate Enforcement and Audit Reports
Elisity's reporting and audit logging streamline compliance audits, making them faster and easier while boosting your team's confidence. Ensure alignment with and adherence to NIST, PCI, HIPAA, 405 (d), IEC 62443, and other frameworks and regulations. Continuous discovery, correlation, and automated policy creation guarantee proactive protection against cyber threats for every device on your network.
-

Accelerate Your Least Privilege Access Strategy
Elisity simplifies the process of applying least privilege access for your users, workloads, and devices, thereby enhancing your organization's protection against east-west attacks. Additionally, Elisity's robust discovery and correlation capabilities ensure that automated policies can be applied to every device, everywhere on your networks. And, Elistiy’s Dynamic Policy Engine enables policies to persist for every device, no matter where or when it appears on the network. Policy groups can be automatically applied based on policy classification details. Ultimately, this means that the chaos associated with unmanaged devices will be eliminated.

Contain Threats and Limit the Blast Radius
Microsegmentation of every device, everywhere on your network, is the best defense against lateral (east-west) movement of cyber attackers. Ransomware and active infiltrators utilize reconnaissance, credentials, and access to move closer to their targets. With Zero Trust explicit access policies for every user, workload, and device on your network, attackers will be blocked and contained.
Learn More
Automate Enforcement and Audit Reports
Elisity's reporting and audit logging streamline compliance audits, making them faster and easier while boosting your team's confidence. Ensure alignment with and adherence to NIST, PCI, HIPAA, 405 (d), IEC 62443, and other frameworks and regulations. Continuous discovery, correlation, and automated policy creation guarantee proactive protection against cyber threats for every device on your network.
Learn More
Accelerate Your Least Privilege Access Strategy
Elisity simplifies the process of applying least privilege access for your users, workloads, and devices, thereby enhancing your organization's protection against east-west attacks. Additionally, Elisity's robust discovery and correlation capabilities ensure that automated policies can be applied to every device, everywhere on your networks. And, Elistiy’s Dynamic Policy Engine enables policies to persist for every device, no matter where or when it appears on the network. Policy groups can be automatically applied based on policy classification details. Ultimately, this means that the chaos associated with unmanaged devices will be eliminated.
Learn More
Resources

RSAC 2026: Essential Agenda Guide for CISOs, Architects, and Zero Trust Leaders

What Is Claroty and How Does It Protect Medical Devices (IoMT & Healthcare OT)

Implementing CTEM Microsegmentation: A Practitioner's Guide to Deployment, Compliance, and Measurable Results (Part 2 of 2)
Ready to Prevent Lateral Movement? Secure Your Network in Weeks, Not Years
Don't wait for attackers to exploit your east-west traffic security policy gaps. Implement Elisity's identity-based microsegmentation without agents, hardware, or network changes. Discover 99% of all users, workloads, and devices in one day, create dynamic least privilege policies, and prevent lateral movement—all while leveraging your existing infrastructure. Schedule your personalized demo today.
Schedule Time With Us



