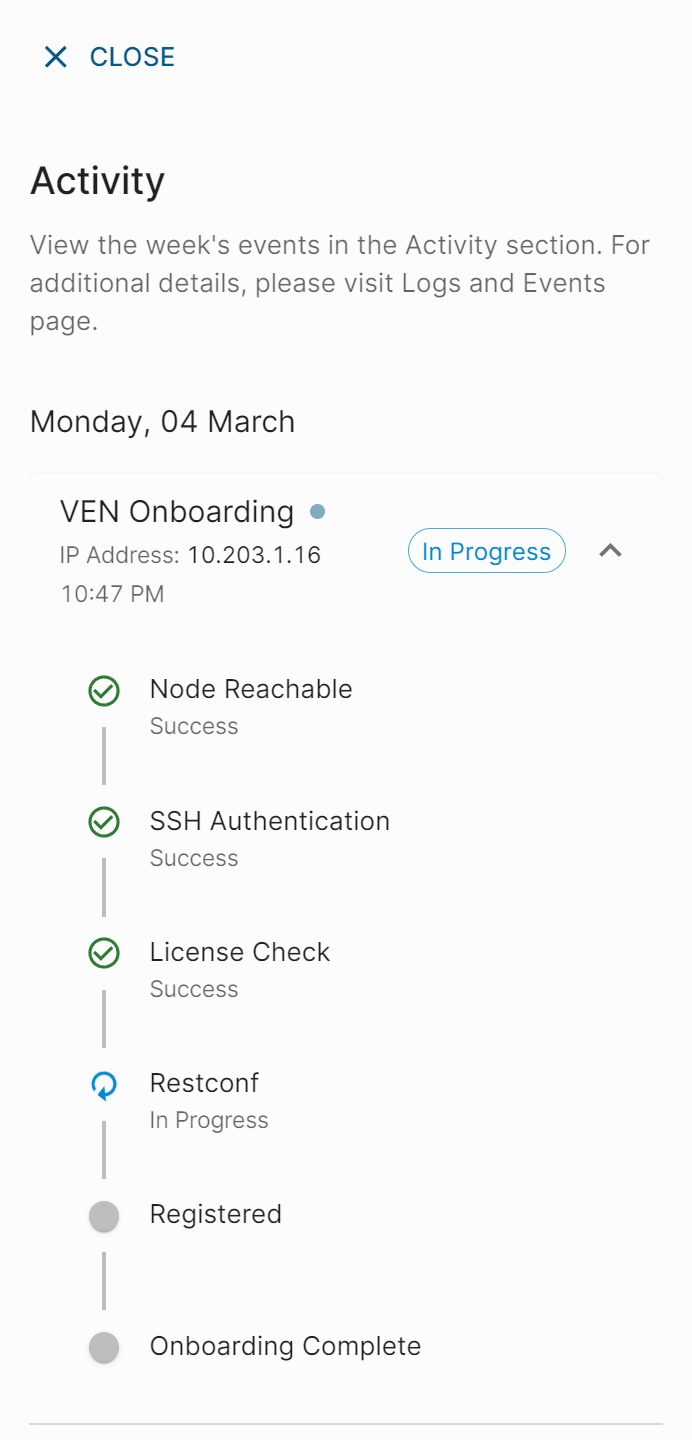
Elisity Releases Version 15.5.0 of their Identity-Based Microsegmentation Solution

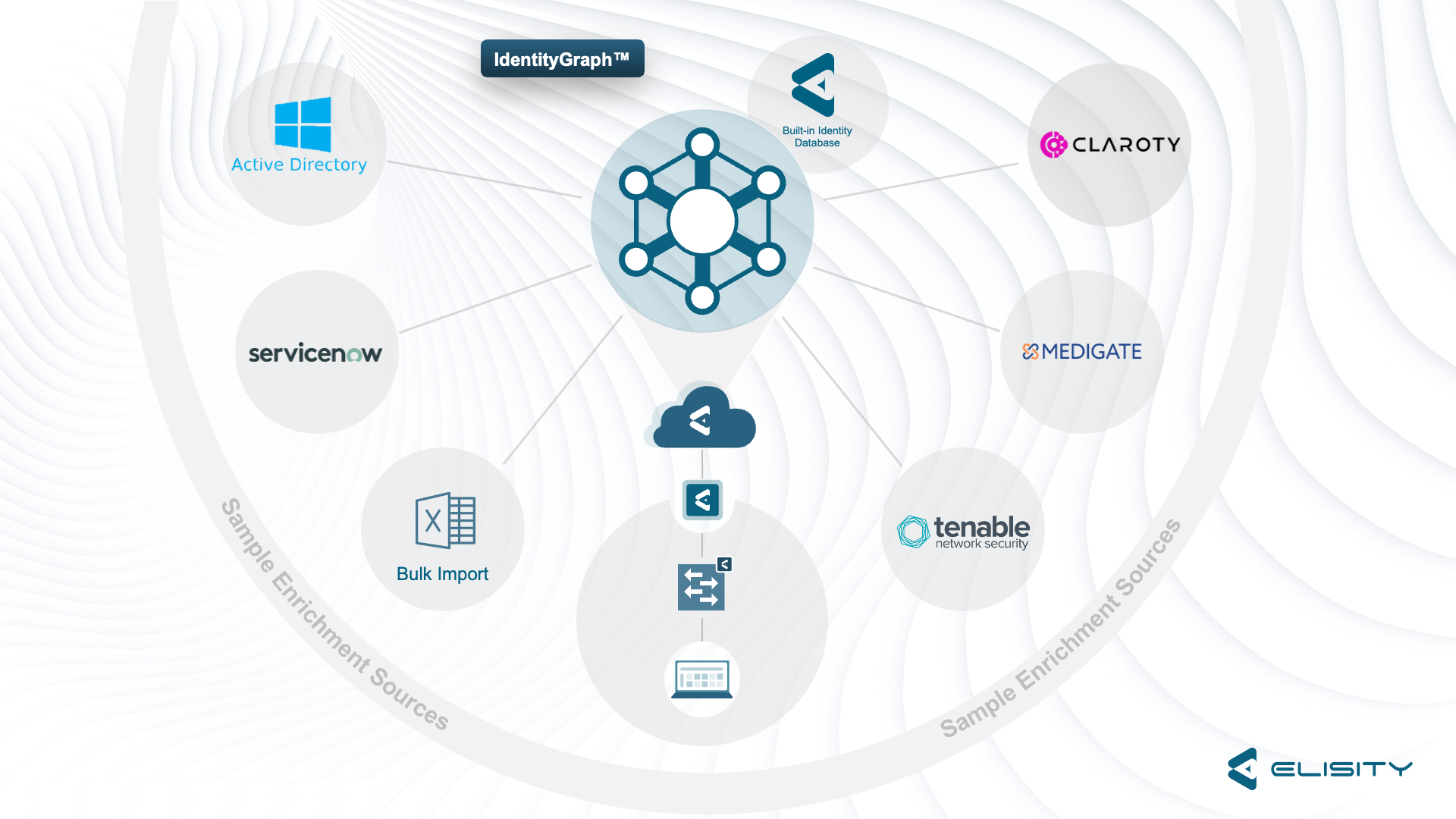
Elevating IdentityGraph™: Introducing Elisity's Latest Integration with CrowdStrike
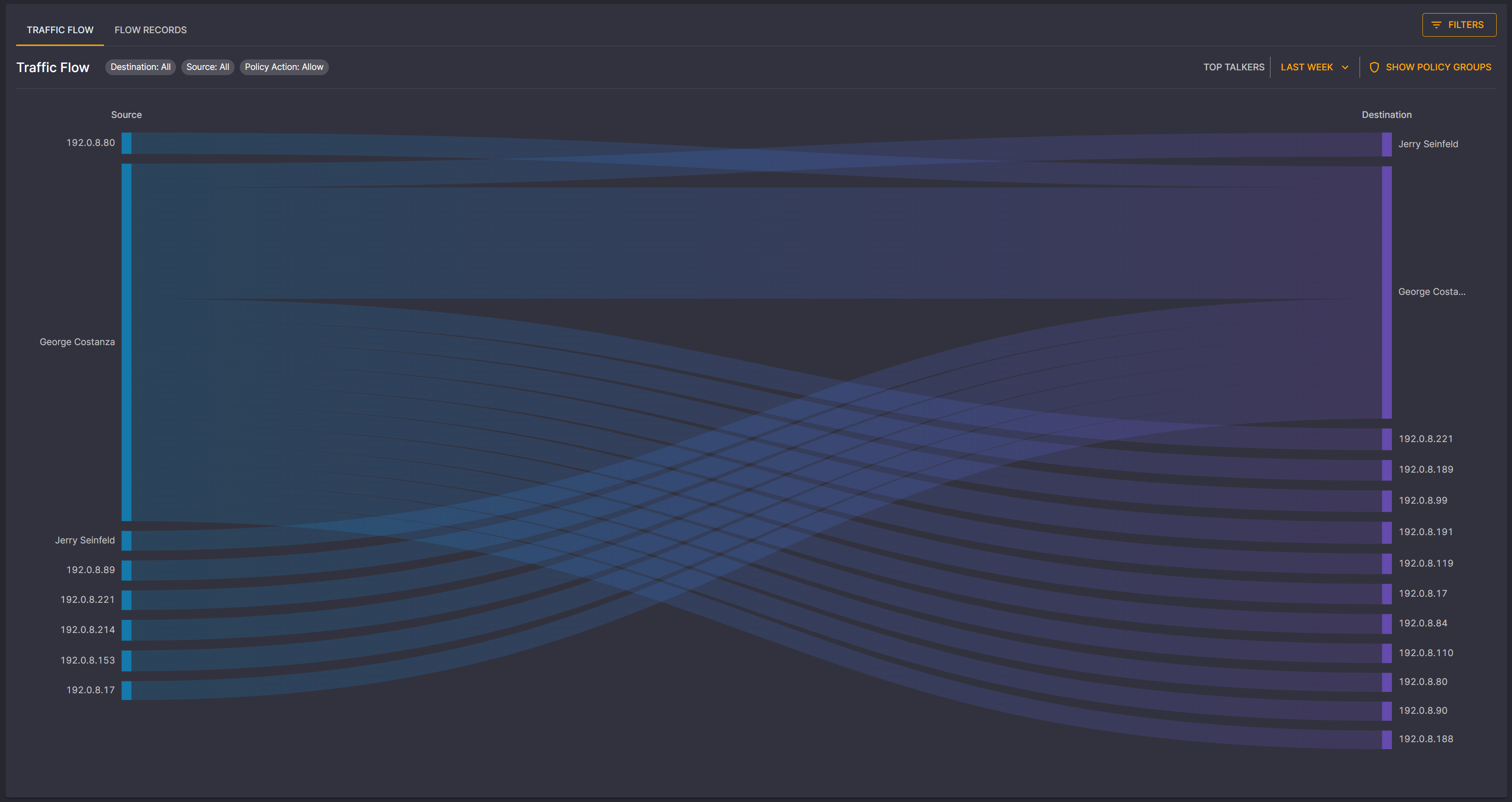
Elisity Releases Version 15.4 of their Identity-Based Microsegmentation Solution
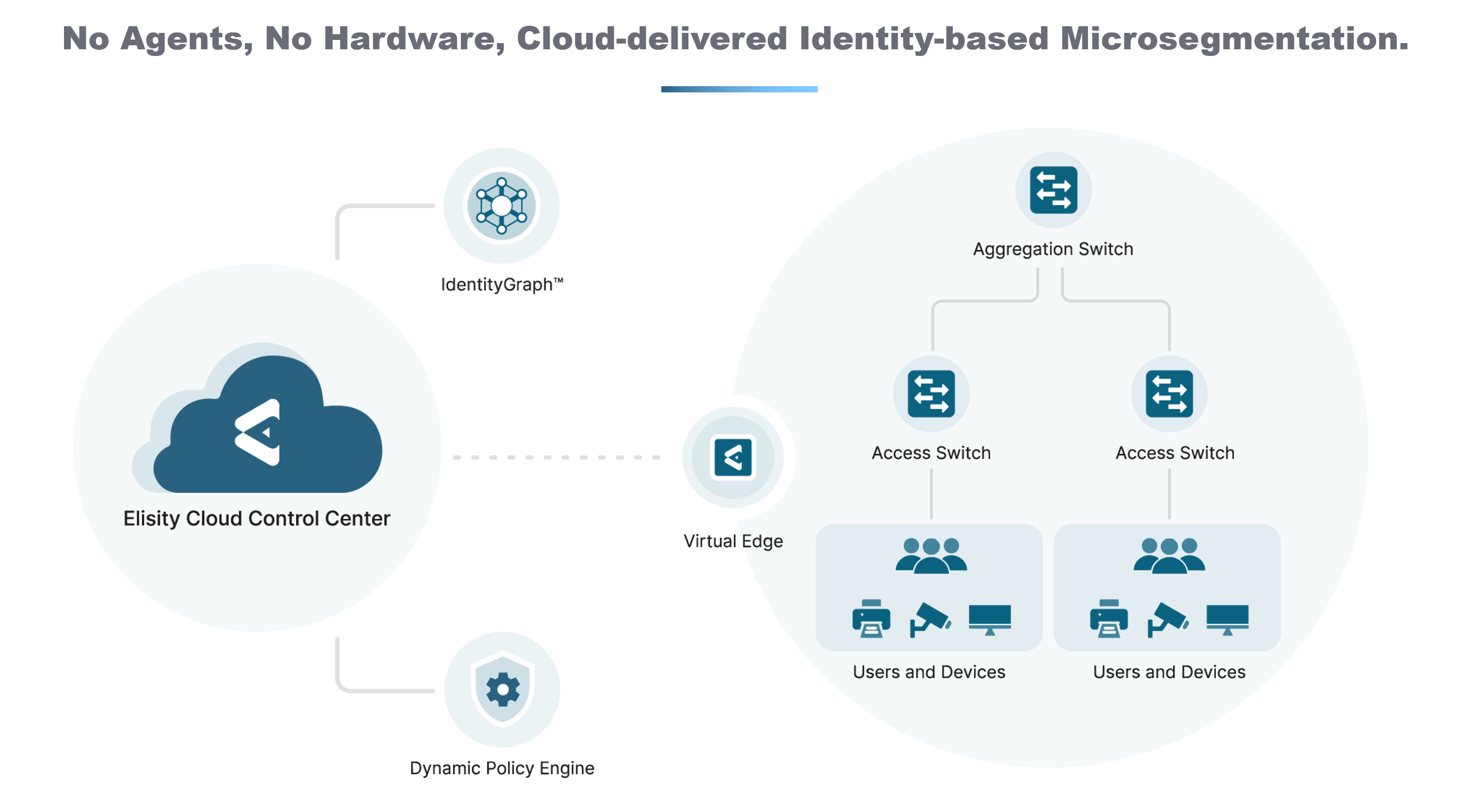
From Vulnerable to Vigilant: Addressing the Top 10 Network Misconfigurations with Elisity
Elisity Releases Version 15.2