Share this
Strengthening Healthcare Security: The Elisity-Armis Integration for Medical Device Microsegmentation
by Dana Yanch on Apr 23, 2025 8:53:05 AM
The Technical Challenge of Securing Medical Devices at Scale
Healthcare organizations face a unique set of cybersecurity challenges when it comes to their expanding IoMT (Internet of Medical Things) ecosystem. A typical hospital network may contain thousands of connected medical devices – from infusion pumps and telemetry monitors to diagnostic equipment and surgical systems – often running legacy operating systems that cannot support traditional endpoint protection.
With attackers leveraging lateral movement techniques in over 70% of successful breaches, organizations need a comprehensive approach to microsegmentation that provides visibility, security, and control. Traditional approaches to microsegmentation often required complex, multi-year initiatives involving agents, firewalls, and extensive VLAN reconfiguration, making implementation particularly challenging in clinical environments where downtime isn't an option, and assets are generally highly dynamic.
Technical Architecture: The Bidirectional Integration
I'm excited to share the details of our bidirectional integration with Armis Centrix™, which addresses these challenges. This technical integration synchronizes data between platforms in both directions, creating a comprehensive security framework that enhances visibility, security, and control.
The integration begins with a secure API connection synchronizing Armis' rich asset intelligence into the Elisity IdentityGraph™. Device attributes from Armis, including risk score, boundaries, device type, manufacturer, model, operating system, firmware version, and network segment, are synchronized to Elisity's IdentityGraph™. These enriched attributes are correlated with data from other sources, including Active Directory, CMDB, and EDR platforms, to create a comprehensive device identity profile. The additional metadata powers our machine learning-based classification engine, enabling more accurate automatic classification of devices into policy groups.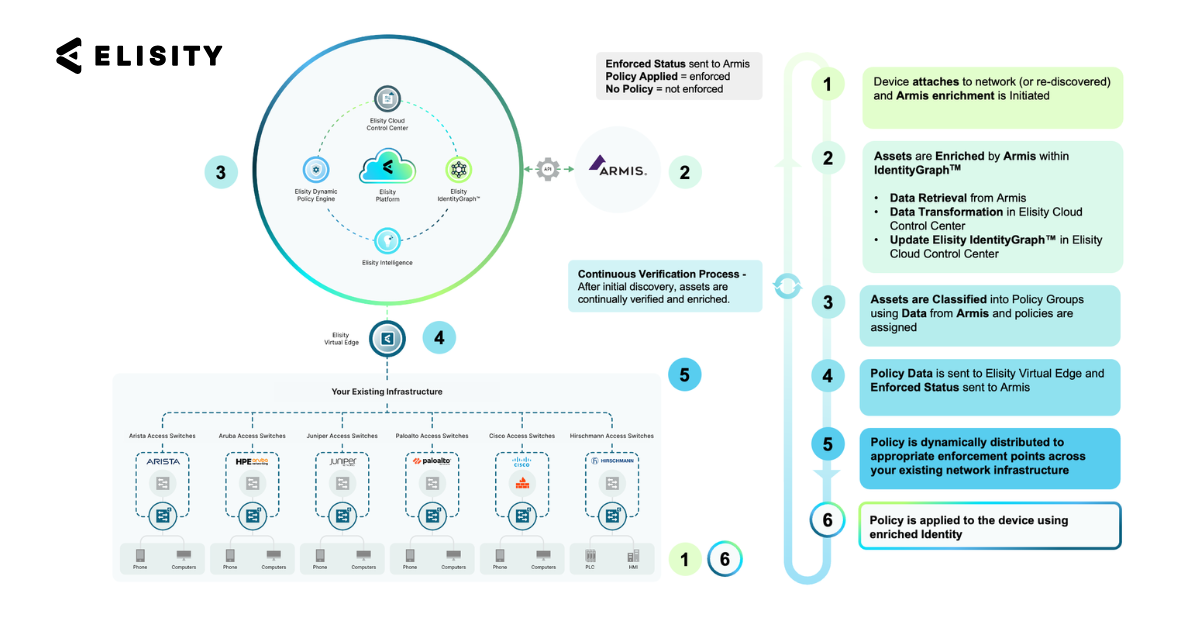
What makes this integration truly powerful is the bidirectional nature of the data flow. Elisity sends critical policy and enforcement information back to Armis. Enforcement status (enforced, not enforced) for each device is synchronized back to Armis, enabling security teams to verify microsegmentation coverage directly within the Armis interface, including flow metadata gathered by Elisity about actual communication patterns between devices that supplements Armis' behavioral analysis capabilities.
This bidirectional data flow creates a unified security framework in which asset intelligence drives policy creation, and policy enforcement details enhance asset intelligence—a true security feedback loop.
Technical Implementation: API-driven Integration
As shown in the diagram, the integration follows a six-step process:
- Device attaches to the network (or is re-discovered), and Armis enrichment is initiated
- Assets are enriched by Armis within IdentityGraph™, with data retrieval and transformation occurring in Elisity Cloud Control Center
- Assets are classified into policy groups using data from Armis, and policies are assigned based on device identity
- Policy data is sent to Elisity Virtual Edge, and enforcement status is sent to Armis
- Policy is dynamically distributed to appropriate enforcement points across the existing network infrastructure
- Policy is applied to the device using enriched identity
Technical Case Study: Main Line Health's Implementation
Aaron Weismann, CISO at Main Line Health, implemented our combined solution to address their complex IoMT security challenges. Their environment included thousands of medical devices, many of which he described as "mini Linux machines" that could become jumping-off points for attacks.
"The synergy between Armis and Elisity has fortified defenses against targeted cyber threats, improving overall operational efficiency with added layers of visibility and security... Microsegmentation is a key strategy for accelerating our Zero Trust program," said Weismann.
From a technical perspective, Main Line Health's implementation began with a discovery phase, which provided passive monitoring for three months to model device communication patterns across their network. Using the aggregated data from both Armis and Elisity, they created granular, context-aware security policies based on device identity and risk profile. These policies were tested in a lab environment and then deployed across the production network, starting with non-clinical areas before expanding to acute care settings.
The bidirectional nature of the integration allowed Main Line Health to continuously refine its policies as new devices were identified or risk scores changed. This enabled them to deploy granular microsegmentation policies with unprecedented speed. "We deployed Elisity at two of our sites in less than an hour, and by the next day, we were confidently implementing policies," Weismann noted.
Technical Benefits for Healthcare Environments
The bidirectional integration delivers several technical advantages specifically for healthcare environments. One of the most powerful capabilities is dynamic policy automation based on risk. By leveraging Armis risk scores, Elisity can automatically quarantine devices when risk scores exceed defined thresholds, adjust allowed communication patterns based on risk level, and apply more restrictive policies to devices running vulnerable software. This dynamic approach ensures that security policies evolve in real time as the threat landscape changes without requiring manual intervention.
The integration leverages machine learning algorithms to automatically classify devices into policy groups based on multiple attributes, including device type, manufacturer, and model information, operating system and firmware versions, communication patterns and protocols, location and department context, and risk score and vulnerability profile. These classification capabilities enable security teams, with the help of AI, to create granular policies without manually defining rules for each device.
A critical technical advantage of this partnership is the ability to implement microsegmentation without requiring agents on medical devices. The integration leverages network-based controls using existing infrastructure, identity-based policies that transcend IP addressing, dynamic enforcement at the network edge, and distributed policy enforcement across multiple vendors' equipment. This approach is particularly valuable for healthcare environments where installing agents on FDA-approved medical devices is often impossible.
Closing the Loop: Comprehensive Visibility and Control
The bidirectional integration between Elisity and Armis provides a technical foundation for implementing Zero Trust architectures in complex healthcare environments. By combining comprehensive asset intelligence with identity-based microsegmentation, organizations can finally achieve the security and compliance they need without compromising patient care or operational efficiency.
This integration represents a significant advancement in network segmentation architecture, enabling security teams to implement microsegmentation in weeks instead of years, even across complex and dynamic environments with thousands of medical devices. The bidirectional nature of the integration creates a continuous feedback loop that enhances visibility, security, and control, helping organizations stay ahead of evolving threats.
As we've seen with Main Line Health's implementation, the joint solution delivers real-world value by enabling healthcare organizations to rapidly deploy microsegmentation without disrupting critical clinical operations. The ability to automatically adjust security policies based on real-time risk information provides a level of protection previously unattainable with traditional security approaches.
Visit our developer portal or contact our solution architects to learn more about this integration's technical implementation or to schedule a demonstration.
Share this
- Enterprise Cybersecurity (60)
- Zero Trust (25)
- Microsegmentation (23)
- Enterprise Architecture Security (14)
- Lateral Movement (10)
- Elisity (8)
- Network Security (8)
- Ransomware (6)
- Identity (5)
- Cyber Resilience (4)
- Cybersecurity Healthcare (4)
- Elisity Release (4)
- Remote Access (4)
- ICS Security (3)
- Identity and Access Management (2)
- Industrial Cybersecurity (2)
- OT Security (2)
- S4x26 (2)
- AI Security (1)
- Agentic AI (1)
- Forrester (1)
- Information Security (1)
- MITRE (1)
- February 2026 (11)
- January 2026 (4)
- December 2025 (4)
- November 2025 (3)
- October 2025 (5)
- September 2025 (4)
- August 2025 (5)
- July 2025 (5)
- June 2025 (5)
- May 2025 (4)
- April 2025 (5)
- March 2025 (6)
- February 2025 (3)
- January 2025 (5)
- December 2024 (4)
- November 2024 (5)
- October 2024 (7)
- September 2024 (5)
- August 2024 (3)
- July 2024 (4)
- June 2024 (2)
- April 2024 (3)
- March 2024 (2)
- February 2024 (1)
- January 2024 (3)
- December 2023 (1)
- November 2023 (1)
- October 2023 (2)
- September 2023 (3)
- June 2023 (1)
- May 2023 (3)
- April 2023 (1)
- March 2023 (6)
- February 2023 (4)
- January 2023 (3)
- December 2022 (8)
- November 2022 (3)
- October 2022 (1)
- July 2022 (1)
- May 2022 (1)
- February 2022 (1)
- November 2021 (1)
- August 2021 (1)
- May 2021 (2)
- April 2021 (2)
- March 2021 (3)
- February 2021 (1)
- November 2020 (2)
- October 2020 (1)
- September 2020 (1)
- August 2020 (3)




No Comments Yet
Let us know what you think