Elisity Named Among Notable Vendors in the Forrester Microsegmentation Landscape, Q2 2024
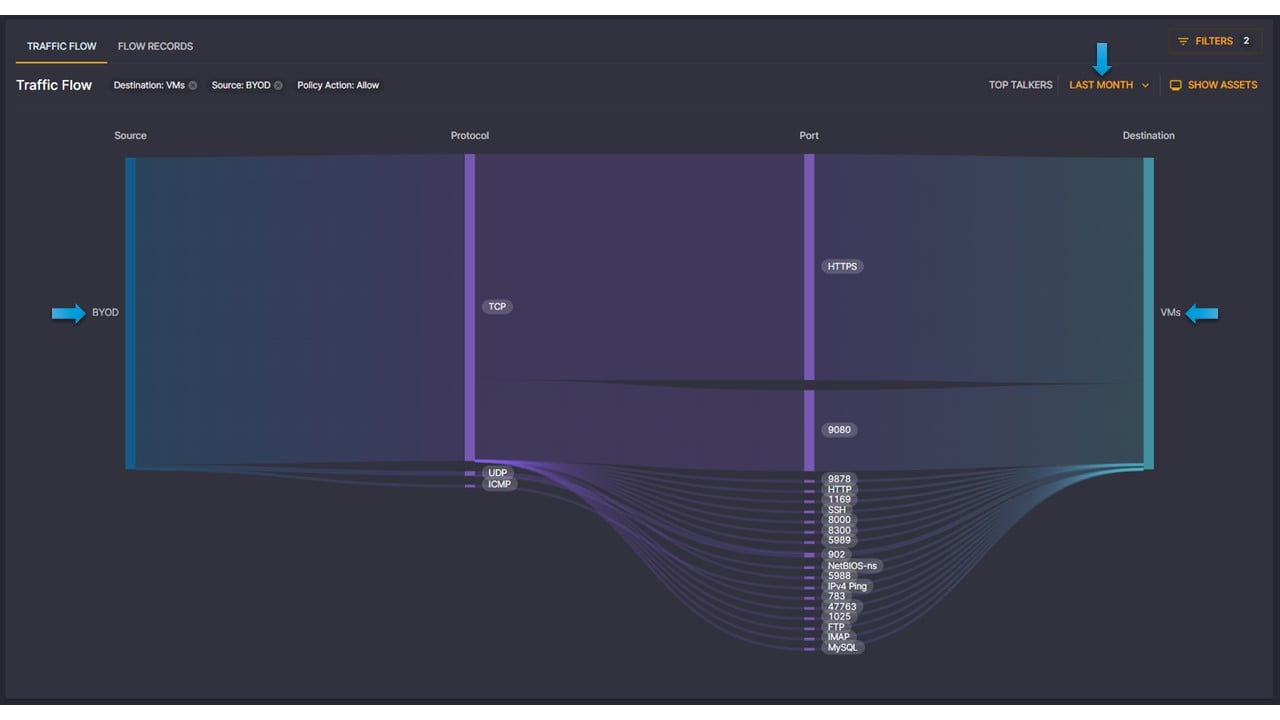

Elisity Named Among Notable Vendors in the Forrester Microsegmentation Landscape, Q2 2024
Apr 23, 2024 12:15:41 PM
2
min read
Introducing Cloud Control Center version 15.6
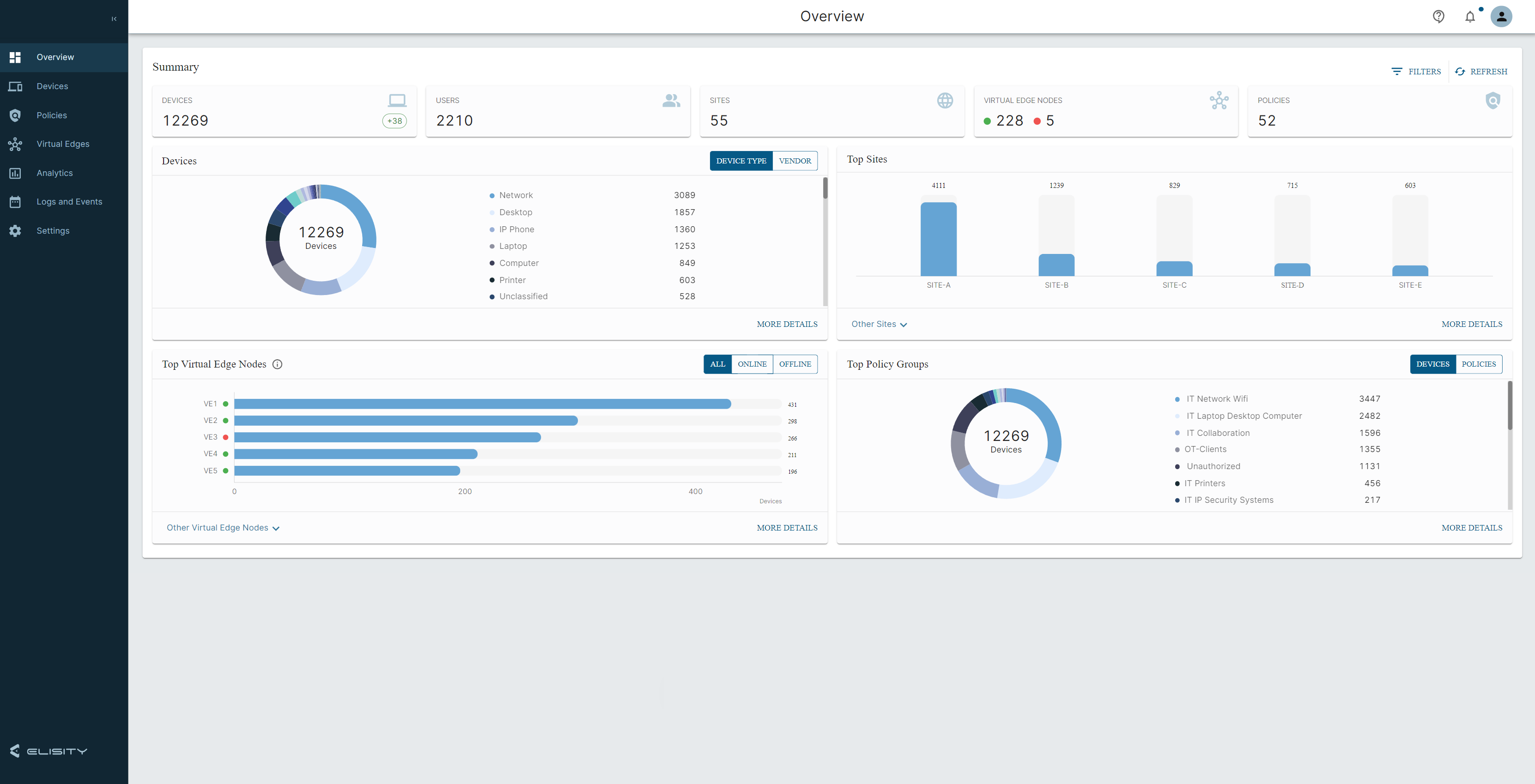

Introducing Cloud Control Center version 15.6
Apr 8, 2024 4:54:33 PM
4
min read
Elisity Releases Version 15.5.0 of their Identity-Based Microsegmentation Solution
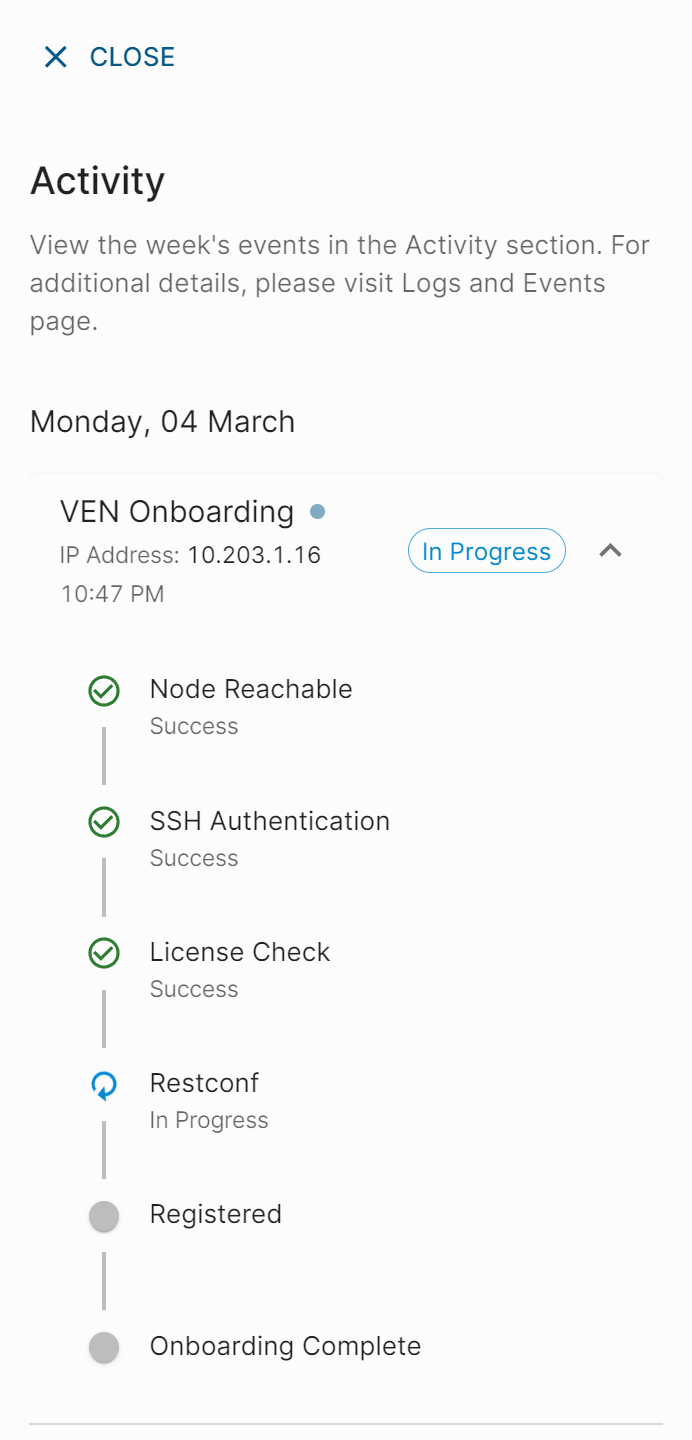

Elisity Releases Version 15.5.0 of their Identity-Based Microsegmentation Solution
Mar 8, 2024 6:28:14 PM
2
min read
Advancing Zero Trust with NSA’s Guide & Elisity’s Solutions


Advancing Zero Trust with NSA’s Guide & Elisity’s Solutions
Mar 6, 2024 9:33:30 AM
4
min read
I Wish We Had Elisity


I Wish We Had Elisity
Feb 19, 2024 10:01:56 PM
8
min read
Elevating IdentityGraph™: Introducing Elisity's Latest Integration with CrowdStrike


Elevating IdentityGraph™: Introducing Elisity's Latest Integration with CrowdStrike
Jan 19, 2024 11:36:25 AM
5
min read
